Storage
Amazon S3 Security Guide
This is a practical guide to Amazon S3 security and your backups in S3. It covers the essentials of identity management, server-side encryption, and endpoint security.
 - everything about backing up to Amazon S3 with MSP360, and more.
- everything about backing up to Amazon S3 with MSP360, and more.
Introduction
There are three main pain points in securing data that is backed up to Amazon S3:
- Securing your Amazon Web Services account
- Securing your Amazon S3 data storage bucket
- Maintaining network endpoint security
We will start this article by explaining strategies for securing your Amazon Web Services account with AWS Identity and Access Management (IAM).
Secure Your AWS Account and Buckets
When you start using Amazon S3 as a backup destination, there are two security considerations to keep in mind:
- Your AWS account
- Access to your Amazon S3 buckets
AWS provides you with several features that help secure both of these items. You can enable AWS S3 encryption and S3 bucket logging to secure your bucket and perform an audit. To secure your account, you should configure AWS Access and Identity Management service (or AWS IAM for short).


Access and Identity Management
In Amazon Web Services, there is one root account that has access to all services and the ability to set up user accounts with granular permissions to the necessary services. These users are created using the AWS Identity and Access Management service, which gives you control over any aspect of any service inside AWS.
Further reading Identity and Access Management in the Cloud
Below, you will find a guide for securing your root account and creating IAM users for backup purposes.
AWS IAM Fast Setup for Amazon S3
1. Let’s start with the basic Amazon S3 security procedures. In the AWS console, find the IAM service and click it. You will then see five security notifications. We strongly recommend going through all of them.
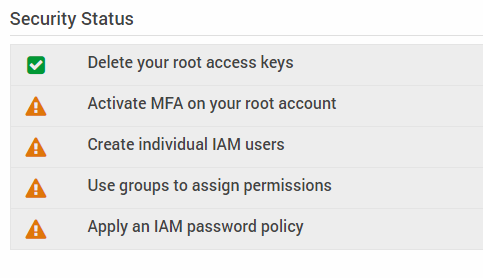
The first option, ‘Delete your root access keys’, is enabled by default. This can be a bit misleading, because many users confuse the “access keys” referred to here with the account credentials they use to enter the AWS web-console. These are different things
Access keys refers to access and secret key, which is a set of credentials that you use to communicate your identity and permissions to AWS services and third-party applications. For example, when you connect to backup software that is capable of performing backup to Amazon S3, you need to enter access and secret keys in that software. You will then be recognized by AWS and allowed to upload/download data to and from Amazon S3.
In AWS, access keys do not exist until you create them. Since you have not created root access keys, AWS thinks that you have deleted them.
Root access keys are a set of credentials that provide access to all services and features of AWS. It's a best practice not to create these keys at all.
Further reading How to Find Your AWS Access and Secret Keys
2. Configure multi-factor authentication (MFA) on your root account.
Since your root account has unlimited power inside AWS, it must be protected. Use a sophisticated password and store it safely. Don’t give your root credentials to others.
3. Create a bucket for your backups.
When you upload/download data to Amazon S3, you store it in what AWS refers to as buckets. You can create as many buckets as you wish. Go to Amazon S3 Console and create a bucket.
4. Create a Dedicated IAM User.
After you have set up the bucket, you need to create an IAM user with permissions for it. If the user already exists, you need to grant it the necessary permissions. To do this, first click Services in the upper left corner of the console and find IAM. In IAM settings, select Users in the menu on the left and click Add user.
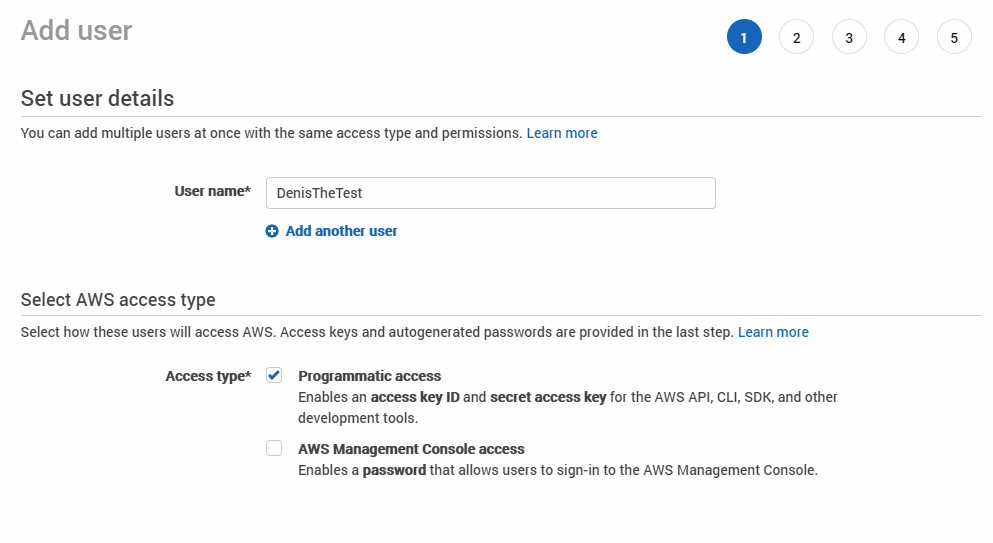
5. Give your user access to your bucket.
First, choose a ‘User name’ and select access type. Access and Secret Keys will be used later in the backup software that you use for data upload. The access key will be visible after creation, but a secret key will only be shown once. If you have forgotten or lost your secret key, you need to create another access and secret key pair.
Click the Attach existing policies directly and Create Policy buttons to choose the needed permissions. Your IAM user needs list, read, and write access to the given bucket to upload, verify, and download the data.
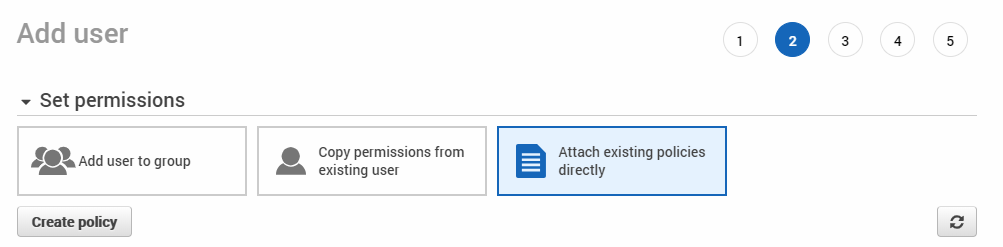
If you plan to have many users upload or download backup data, creating a dedicated user and a corresponding set of permissions will be time-consuming. In this case, you can save time by granting permissions to a group. Each user added to the given group will have the same set of permissions.
You have now created your first bucket and user for backup operations. If you have any setup questions, don’t hesitate to ask on our forum.
IAM best practice: Give only the minimal required permissions
AWS IAM In-Depth
If you are going to leverage other AWS services, check out our in-depth Amazon S3 security articles. They will help you to get used to using AWS IAM and help you set up flexible permissions for various users and services.
Further reading AWS Security In-Depth 1: ACLs vs Bucket Policies vs IAM
Further reading AWS Security In-Depth 2: IAM Policies
Further reading AWS Security In-Depth 3: IAM Identities
Amazon S3 Bucket Security and Data Protection
There is a risk that your data in the cloud will be compromised. Security has been one of the biggest concerns about cloud services from the very beginning. To protect your cloud data from unauthorized access, you need to encrypt it. AWS has several features and services for Amazon S3 bucket security.
AWS S3 Encryption
While uploading data to Amazon S3, you can enable the server-side encryption (SSE) option. Once this is enabled, each file is encrypted as soon as it reaches the S3 bucket. This protects your data in the event that hackers get direct access to AWS data centers.
Only users with sufficient permissions to download the data can access it.
By default, AWS does not allow public access to your data, meaning it is invisible from the Internet by default. You can enable public access manually, but we don’t recommend doing so.Most data breaches happen when someone grants public access to files. If you need to share data with a third party, create a dedicated IAM user with limited access.
Remember: Enabling server-side encryption and giving public access to data is. By doing this, you give full data access to anyone on the Internet, and files will be automatically decrypted once the data is requested.
Further reading How to configure Amazon S3 Server Side Encryption
Key Management Service
To enhance server-side encryption, AWS offers the Key Management Service. With it, you can create and manage encryption keys for data in your S3 buckets. Users without a key ID cannot access the data. Therefore, if the user account is compromised, but the key ID is safe, your data is also safe.
KMS keys can be used in the same region in which they were created.
Further reading Using MSP360 Backup with AWS KMS
Enable Amazon S3 Bucket Logging
Amazon S3 bucket logging allows you to monitor the activity inside an S3 bucket. It is helpful if you have many files, buckets, or users. Bucket logging is a great tool for performing security audits.
Further reading How to Enable and Read Amazon S3 Bucket Logs
Client-Side and In-Transit Encryption
Even a bulletproof AWS account won’t keep data secure if data is not protected on the user's end. There are three ways to protect your data against three main dangers:
-
- File encryption against direct data breaches.
- Filename encryption to prevent attackers from seeing the names of files, which can reveal sensitive information. This can be a concern if your data falls under GDPR compliance rules, for example.
- Secure transfer channels to prevent transfer breaches.
Encrypted data is defenseless against ransomware. Often a virus hits files, which are then backed up to the data storage. They will replace the previous backup and you are left with no other options than to pay the ransom and literally hope for the best.
To prevent that, you should set up backup versioning for (at a minimum) mission-critical data. That way, if your latest backup is cryptolocked by ransomware, you still have one version before that from which you can recover.
Further reading How to Protect Against Ransomware
Secure Backup to Amazon S3 with MSP360 Backup
At MSP360, we have developed reliable software for S3 backup that meets stringent security standards. MSP360 Managed Backup for Amazon S3 supports object lock (immutability), ensuring your backup data is securely protected against any unauthorized modifications.
Additionally, MSP360 Managed Backup enhances data security with user-generated encryption passwords, file name encryption, and secure data transfer. Our solution also enables MSPs and IT teams to work safely with their access and secret keys, as it fully supports IAM roles, providing an extra layer of security and control.

Backup to any Amazon S3 Class
Cut costs by leveraging the lower-cost Amazon S3 IA and Amazon Glacier storage with MSP360 Managed Backup and Standalone Solutions

Amazon S3 Intelligent Tiering Support
MSP360 Backup provides the ability to back up data directly to the Intelligent-Tiering storage class.
Lifecycle and Retention Management
MSP360 Backup fully supports data versioning in Amazon S3. When creating a backup plan, you can create a flexible and automated retention policy.
 AWS IAM Support
AWS IAM Support
MSP360 Standalone Backup securely works with your access and secret keys. Our SaaS solution - MSP360 Managed Backup - works directly with IAM users to ease management and deployment for multiple users and organizations.
Conclusion
If you have:
- Up-to-date antivirus and firewall protection
- Encrypted files and filenames on the computer
- Ensured that data transfer is encrypted
- Set up Amazon S3 SSE
- Created a user structure with minimal permissions in AWS IAM
The chances of losing your data due to poor security are close to zero. For more security articles, check out this guide on Google Workspace Security.
Just don’t leave your password on a sticky note around your desk!


