Security
Methods and Types of Phishing Attacks
The internet can be a dangerous place no matter how tech-savvy you are. Massive data breaches have become a part of the daily news cycle, mainly because of the vast number of hackers out there looking for new ways to infiltrate systems and steal private information.
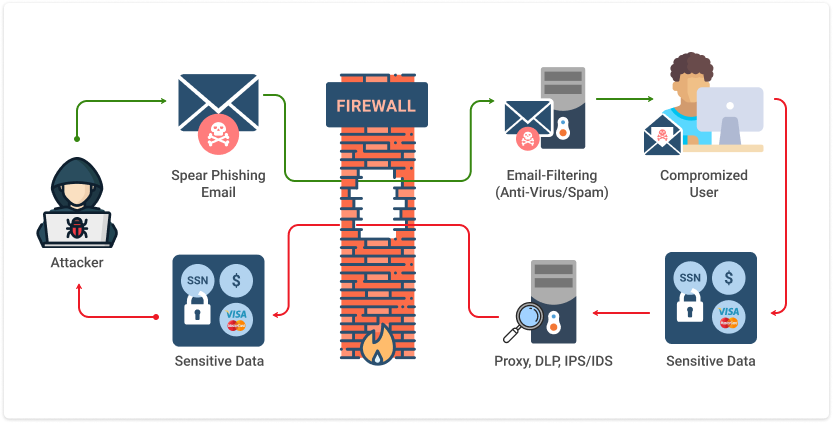
But often the most damaging cyberattacks occur on a smaller scale through a form of hacking known as phishing. With various types of phishing attacks, the criminal sends a fraudulent communication (typically email) that claims to be from a reputable organization. These can be hard to distinguish from legitimate messages, but if you fall for it, the hacker may help themselves to your passwords, credit card numbers, or other sensitive data.
Let’s run through the different types of phishing attacks and the most common methods hackers are using to perpetuate them in the real world today.
For more information about phishing please refer to our guide on the topic:
Further reading Anti-Phishing Guide
Types of Phishing
Spear Phishing and Whaling
 When a phishing attack bypasses the large, generic group target strategy, and instead pursues a specific person, organization, or company, it becomes classified as spear-phishing. Typically the message will contain the recipient's name or other identifying information to lend a flavor of credibility.
When a phishing attack bypasses the large, generic group target strategy, and instead pursues a specific person, organization, or company, it becomes classified as spear-phishing. Typically the message will contain the recipient's name or other identifying information to lend a flavor of credibility.
Whaling is a specific type of spear-phishing that aims to target executive-level employees at major companies. These fraud messages look more professional and warn the recipient of issues with their technology accounts. If the upper-level person divulges a password or piece of critical information, it can put the entire operation at risk.
Further reading How to Prevent Spear Phishing Attacks
Clone Phishing
 Clone phishing is a subtype of spear-phishing that aims to replicate another email message that the recipient has previously received. For example, if the hacker can determine that a person recently received a shipment tracking email notification, then they may launch a clone phishing attack that sends a fraudulent message tailored to look like the same thing.
Clone phishing is a subtype of spear-phishing that aims to replicate another email message that the recipient has previously received. For example, if the hacker can determine that a person recently received a shipment tracking email notification, then they may launch a clone phishing attack that sends a fraudulent message tailored to look like the same thing.
Further reading Clone Phishing Explained
Check out these marketing templates that we created to help MSPs sell Microsoft 365 as a managed service:

Phishing Methods
Link Manipulation
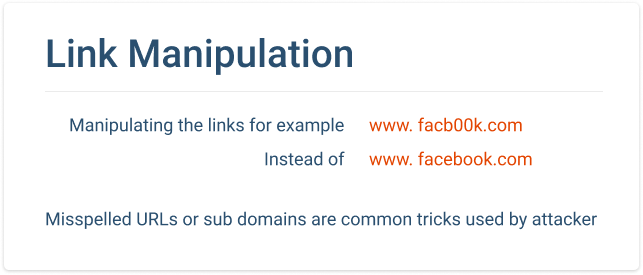
The most common types of phishing attacks are designed to convince users to click on a malicious link in a fraudulent email. It may redirect the person to a rogue website that will urge the person to divulge a password, credit card number, or other pieces of identifying information.
Phishing emails can be tricky to detect because of link manipulation. Hackers will disguise their malicious URLs inside of an HTML hyperlink that will have a label that looks to be harmless.
If you hover over the hyperlink in your mail application, you will be able to see the true URL hiding.
Filter Evasion
 Every top email provider or client application includes a junk mail filter tool that automatically scans incoming messages and flag ones that have a high likelihood of being malicious in nature. Hackers realize this and design their phishing attacks to circumvent the blocks.
Every top email provider or client application includes a junk mail filter tool that automatically scans incoming messages and flag ones that have a high likelihood of being malicious in nature. Hackers realize this and design their phishing attacks to circumvent the blocks.
The most common tactic in filter evasion is for the hackers to embed links or text within table cells instead of in plain HTML text. This makes it harder for the filter scans to treat the text as a regular string of characters and may allow the message to slip through the cracks.
Website Forgery
Links from these types of phishing emails often lead to suspicious websites that will attempt to clone pages from a reputable company, including banks and retailers. The hacker will design their website with forged content that may disguise the URL in the browser or the SSL certificate.
Covert Redirect
Even if you verify that a link from an email points to the proper URL, it does not mean that clicking on it is safe. Due to a vulnerability known as a covert redirect, hackers are able to exploit an authentication method on certain websites and introduce a pop-up window that is capable of stealing your username and password.
Social Engineering
The concept of social engineering covers a range of scenarios where a cybercriminal tries to gain your trust in order to steal credentials or other identifying information. Such an attack usually involves psychological manipulation, or even establish real-world relationships built over time that carry over into the online space and result in the victim developing trust of the attacker.
Further reading Social Engineering Prevention
Voice Phishing
Voice phishing is a newer trend that is spreading across much of the world. During these types of phishing attacks, you receive a series of calls to your mobile or landline phone from a computerized or human source. The attacker will usually pose as a bank or utility company notifying you about an issue with your account. This is a scheme to gain your trust so that you will provide your credit card or social security number over the phone.
Tips for Protecting Yourself
Due Diligence: Educating yourself on the evolving particulars of different types of phishing threats and staying vigilant are the two primary ways to avoid becoming a victim. Every time you receive an email with a hyperlink, double-check the sender and verify the URL. Laziness or complacency can lead to a costly mistake.
Secure the Connections: If you use a public wi-fi network, be even more careful about how you connect online. Lurking near these spots, which are rarely secured, is a favorite bad guy strategy that almost guarantees access to private information. The best way to fight back is by installing a virtual private network (VPN). This service has gained recent popularity as perhaps the best anonymity and security tool at your disposal. Given the rising risk climate, consider a VPN mandatory any time you’re online.
Hidden Risk in Data Center Downtime: You might think breach attempts on your web host servers are their problem, but the reality is that purveyors of malware strains like Venom bypass connections and trick your host into going into emergency maintenance mode. During this downtime, malware is introduced that allows a hacker to take over a data center and all the websites stored on servers. It’s the ultimate inside job.
Given the preceding, it’s critical to find an ISP with a defensive mindset and reliable uptime. This means they have less exposure to Venom-style attacks. As community-run research group HostingCanada.org found in a multi-year review of popular web hosts, the top hosting companies ranged widely in uptime - between 97.65% to 99.99%. The difference - 2.34% - is equivalent to nearly eight and a half days of downtime over the course of a year.
That tells you how long each web host was down and vulnerable to attack.
The Bottom Line
Different types of phishing attacks represent a serious threat to online security for every person with a computer, tablet, or smartphone. Hackers see it as an easy way to trick people into divulging sensitive information.
If you're not careful, you can end up on a dangerous website or open a malicious file and find yourself under a sudden virus attack. To avoid this unpleasant scenario you should understand the risks and know about various types of phishing. Hopefully, this guide helps with that.