Cyber attacks aimed at breaking through network monitoring defenses and raiding Industrial Control Systems (ICS) and mangling the Industrial Internet of Things (IIoT) is nothing new.
These kinds of attacks have been around since the first company website was launched. From stealing data to altering information to shutting down software and hardware, the threats are there and growing more sophisticated every day.
While some threats are designed to penetrate any type of network or system, Triton is the first malware aimed specifically at breaching ICS and IIoT. Never mind that spyware, ransomware, and crypto jacking get more attention. Triton is as ugly as it gets because it aims to turn off or circumvent safety systems, paving the way for events (such as a deadly chemical release, explosions, or out-of-control fire) that can lead to loss of life.
Further reading Responding to Ransomware: From Detection to Damage Control
Further reading Cryptojacking: How to Detect and Avoid
Here’s what you need to know about Triton malware, including what can be done to safeguard your corporate network and connected equipment.
Triton’s History from 2010 to the Present
Triton’s can be traced to Stuxnet and events in 2010. During that year, the Stuxnet campaign was developed as a computer worm capable of gaining control of programmable logic controllers and changing how they managed the automated functions of industrial machinery.
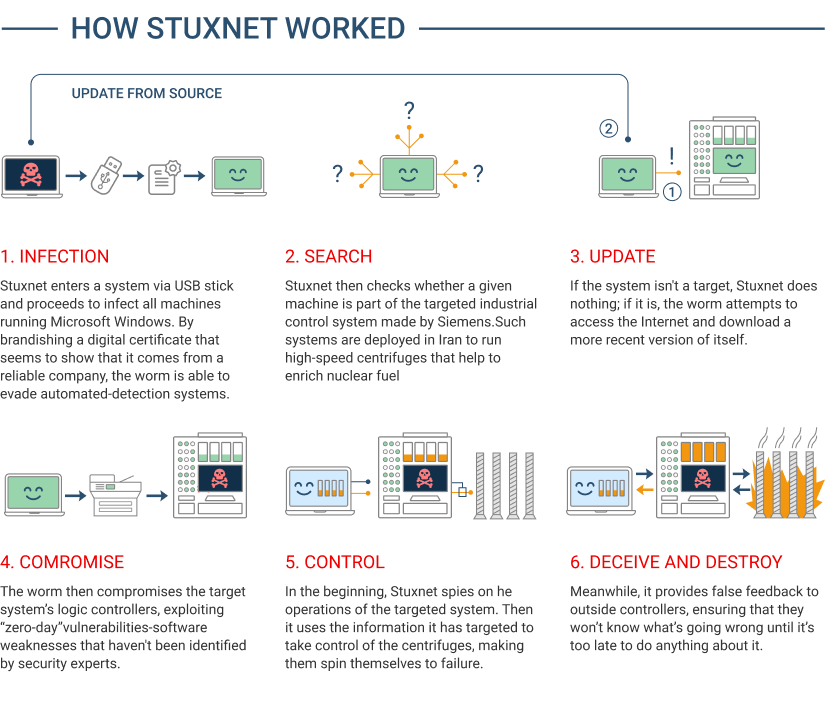
The original idea behind Stuxnet was to develop a worm capable of undermining Iran’s nuclear facility functions. It wasn’t long until the worm was hijacked and adapted by third parties to wreak havoc on everything from power plants to water treatment facilities.
Transmitted via sharing USB sticks and through the Windows systems of the day, it was the first worm that successfully infiltrated and shut down hardware used to control machinery.
Stuxnet Toughens Up and Changes Names
Continued development by multiple groups led to the development of Triton in 2017. During August of that year, the new-and-improved malware emerged as a more dangerous variant of Stuxnet, one capable of disrupting and even destroying production processes. It was discovered by total fluke when a petrochemical plant in the Middle East shut down unexpectedly.
Alternatively dubbed Triton, Trisis, and Hatman, the malware is still infecting thousands of computers and still capable of being transmitted through multiple means. Far from being neutralized as a threat, it continues to be refined and remains one of the most sophisticated threats to corporations today.
Understanding ICS and How an Attacker Gains Entrance
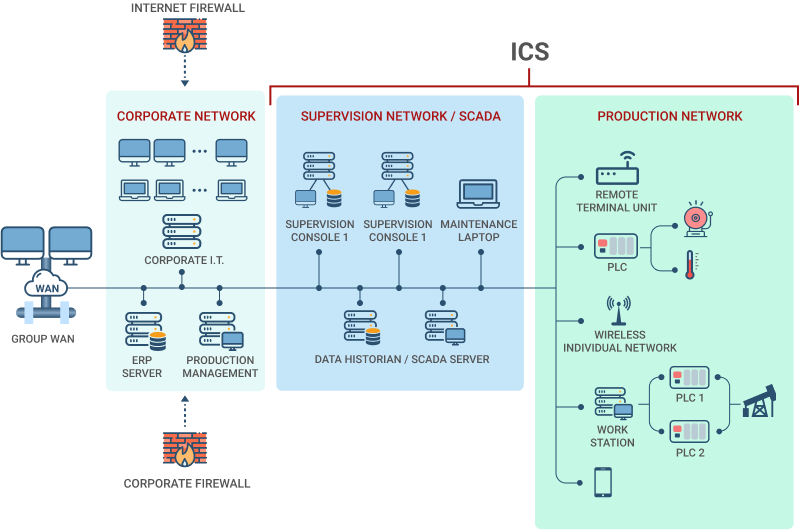
Knowing a little more about ICS (Industrial Control System) & IIoT and how malware infiltrates corporate networks helps illustrate why threats like Triton should not be taken lightly. As the name implies, an Industrial Control System makes it possible to centralize the control of multiple pieces of equipment. That control may be housed in machinery located in a single facility or be networked to control machinery at multiple locations.
Worms and malware gain entrance in a number of ways.
A backdoor approach is to gain network access via infected attachments distributed by email. Using a service to protect your network and monitor websites can often detect backdoor access, but malware programs adapt to circumvent these defenses using a clever form of IP masking to take control of industrial controllers. Once opened, the worm bores into other network files and functions, making it possible to infect the ICS hardware. At that point, it’s easy to shut down or otherwise interfere with the function of the plant machinery.
Infections can also spread via websites as well as file-sharing in supposed safe environments. And as with the original Stuxnet, there is the potential for sabotage to occur by introducing the malware to a system via USB stick.
There’s a good chance your IT team is already doing what they can to close doors to ransomware and crypto jacking, the two most popular malware today. Ransomware seems to be on the decline, though occurrences of crypto jacking continue to rise. Expect threats like Triton to become more common, which makes now a good time for IT teams to become familiar with preventing, detecting, and mitigating it.
First and Second Stages of the Attack
Your network defenses should already ward off a number of threats each day. A robust and regularly updated firewall is a good idea. If you haven’t already, appoint someone on the IT team to make sure your firewall is always up to date. This applies even if you operate a small business.
At the second stage, the threat breaks into the network. There is only a limited amount of time to find and neutralize it, so moving quickly is paramount.
In addition to a strong firewall, ensure your antivirus software is updated at least once a day and that there are network fail-safes that effectively wall off access to data and functions when a threat is detected. Regular software updates may seem like a trivial matter, but they are essential to keeping out malware like Triton. It’s no surprise that FINRA ranks “security updates” as second on their business cybersecurity checklist.
Beyond a firewall and AV software, recommended industrial cybersecurity solutions now include a virtual private network (VPN). No longer a niche tool for security experts and content pirates, the strongest and best VPN services on the market today serve as a means to encrypt data and establish and maintain online privacy through anonymity via IP address shielding. It’s harder for the bad guys to penetrate a network if they can’t find it in the first place.
Detecting the Attack
There is good news in all this. Just as malicious software has evolved, system protections, bolstered by artificial intelligence (AI) improvements, are more sophisticated than ever.
When your protections detect a threat, two things need to happen.
- Access to data and system functions are blocked at once. Passwords can be used to initiate the blocks if necessary.
- Isolating and destroying the threat is essential. This isn’t as easy as it may seem since the nature of worms is to duplicate and then infiltrate all sorts of stored files.
Mitigating the Attack
Recognition is the key to bringing an attack to a halt. At the risk of making the point repetitive, this means keeping protections updated at all times. Most credible virus protection software offers daily patch releases to thwart emerging threats. By applying these patches as soon as they come out, the chance is better that you’ll catch and contain the threat.
There should be an incident response team, armed with a security incident response plan, trained to step in and deal with a detected threat. The purpose is to have a preordained process to contain the threat, determine how to deal with it, and ultimately wipe it from the system before any data can be manipulated or stolen.
Protect Yourself by Upping Your Backup Game
While taking care of a threat while it’s in progress is great, organizations should plan for failure and that means a fail-proof backup plan. In the event the Triton worm succeeds, you will need to shut down, cleanse the system, and then install the most recent clean backup.
The backed up files should be inaccessible to the worm that’s tainting the primary system. One option is a secondary server that can’t communicate with the primary one without authorization or else some type of secure cloud storage. Daily updates will ensure little data is lost if an attack breaches the primary system.
The Bottom Line
Stay on top of the latest protections and take nothing for granted. Ensure your IT team is constantly looking for information on new threats and how to neutralize them. With worms and other forms of malware becoming more complex every day, you can’t afford to be caught off guard by something as nasty as Triton.






