Spear phishing attacks are executed through the use of electronic or email communications. Targeted phishing may impact an individual, corporation, or business, depending upon the objectives and intentions of its perpetrators. Cybercriminals may launch spear-phishing attacks for the following reasons:
- To steal sensitive data such as credit card information and account credentials for financial gain
- To install malware on a targeted device for malicious intent
- To target an organization for securing trade secrets and confidential data which is later resold to competitors
- To acquire military information
A staggering 95% of fraudulent activity which is conducted against enterprises with the sole objective of gaining sensitive data is conducted via spear phishing. In the last two years, email communications scams have caused companies to suffer financial losses of more than two billion dollars according to the FBI. This illustrates the colossal scale of spear phishing attacks that take place globally.
For more information about phishing please refer to our guide on the topic:
Further reading Anti-Phishing Guide
How Does Spear Phishing Work?
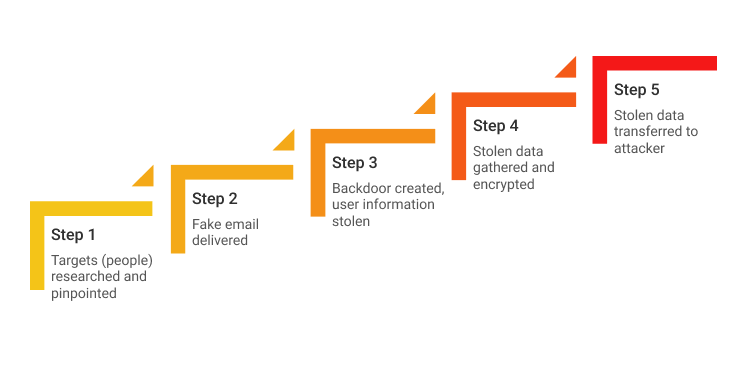
How does spear phishing work?
Spear phishing email attacks are more sophisticated in nature compared to phishing attacks because they are customized for specific victims. Cybercriminals hunt through the Internet to find their targets and record personal information about them, such as their email addresses, hobbies, and recent purchases by probing their social media accounts. Based on this data, they carefully draft spear-phishing emails, assuming the identity of someone the victim can trust.
The messages delivered to recipients create a sense of urgency and compel the victims to share their personal information, such as passwords and credentials. Spear phishing email examples include requests to click on links that direct recipients to websites where they are asked to provide their access codes, PINs and account passwords, or to download malware.
After gathering this information through targeted phishing, criminals make use of data to enter victims’ bank accounts or even create fake online identities. Perpetrators of these scams disguise themselves as friends of the victim or a reliable entity, which makes it difficult to distinguish between legitimate and fraudulent messages without proper spear phishing training.
For more information about other phishing types and techniques please refer to our corresponding guide:
Further reading Methods and Types of Phishing Attacks


How to Prevent Spear Phishing Attacks?
Are you wondering how to prevent spear phishing attacks to protect your users and their private information? Fortunately, there are a number of tried-and-tested measures that you can deploy to combat this menace and stop spear phishing attacks.
#1 Filter Your Email and Implement Anti-Phishing Protection
Besides traditional email security solutions such as anti-spam and antivirus filters, extra anti-phishing software should be implemented (spear-phishing emails usually contain no malware and are almost never spam, which is why they often easily bypass traditional security mechanisms).
There are several useful anti-phishing protection techniques that you can make use of. These include checking for domain spoofing, any instances of impersonation, and flagging questionable content in the email. From an enterprise perspective, there are several reputed organizations such as PhishLabs, IronScales, and PhishMe which are progressively working to protect corporations from becoming victims of these scams.
#2 Keep Your Systems Up-To-Date With the Latest Security Patches
While viruses might be delivered via email, they can be spread across your network using gaps in security caused by outdated software. This is precisely why it is fundamental for individual users and organizations to update their security software regularly to build a wall against possible spear-phishing attacks.
#3 Encrypt Any Sensitive Company Information You Have
Data encryption should be the foundation of your security strategy and is a must-have tool in your arsenal. Encrypting sensitive information essentially makes it impossible for cybercriminals to access data, shutting down or at least weakening their attempts to attack the system.
#4 Conduct Multi-Factor Authentication
This data protection method only unlocks sensitive information upon the completion of an authentication process which has two or more steps. It is a means of applying additional security layers and locking confidential information with more than just a password.
Further reading Multi-Factor Authentication (MFA) as a Must-Have for MSPs
#5 Use DMARC Technology
DMARC stands for Domain-based Message Authentication, Reporting & Conformance technology. The purpose of this mechanism is to evaluate incoming emails against a database with a complete record of the senders. If an email does not align with the information of the sender as recorded in the database, an automatic email is sent to notify the security admin.
#6 Run Frequent Backups
In the event of a successful attack, you need to get users back to work quickly by getting them access to the latest versions of uninfected files. Having a cloud-based backup solution is critical to keeping users productive during a spear-phishing attack.
#7 Conduct Email Security Training for Employees
Security awareness sessions, including spear phishing training, are vital in order to equip employees with the knowledge to identify and divert incoming attacks, particularly at the enterprise level.
#8 Be Wary of Suspicious Emails
Spear phishing emails are becoming increasingly sophisticated. If you receive an email that seems to be from someone you know, but is suspicious of its intent and content, as a best practice, check to see if the person actually sent the message to you.
For more phishing prevention best practices please refer to our corresponding guide:
Further reading Guide on How to Prevent Phishing
Win the Battle Against Spear Phishing
The abundance of personal information and data on the Internet has become a goldmine for cybercriminals to dupe unknowing victims. By staying vigilant and exercising tested tips to dodge spearfishing attacks, you can protect your users from falling into this trap.




