When you think of a modern-day hacker, chances are you picture a shady character camped out behind a sea of monitors, working all day and night to infiltrate networks and systems through fancy coding and password cracking.
In reality, a lot of the cyber attacks and data breaches that have surfaced in the news recently are actually brought about in a much simpler manner. The critical weaknesses are the gullible humans who sit behind computers around the world; hackers have found creative ways to use that gullibility to their advantage.
This article explores the risk of social engineering attacks as well as methods for protecting against them. With online privacy such a precious commodity, it's more important than ever to be on the lookout for this kind of hack.
For more information about phishing please refer to our guide on the topic:
Further reading Anti-Phishing Guide
Social Engineering Meaning
Social engineering is a catch-all term in the cybersecurity industry and one that has taken on new meaning in the internet age. In fact, some of the earliest forms of this type of cyber attack date back to the beginning of the world wide web. Back then, it was easy to trick new internet users into divulging confidential information. Though technology has evolved a lot in recent decades, the same threat remains.
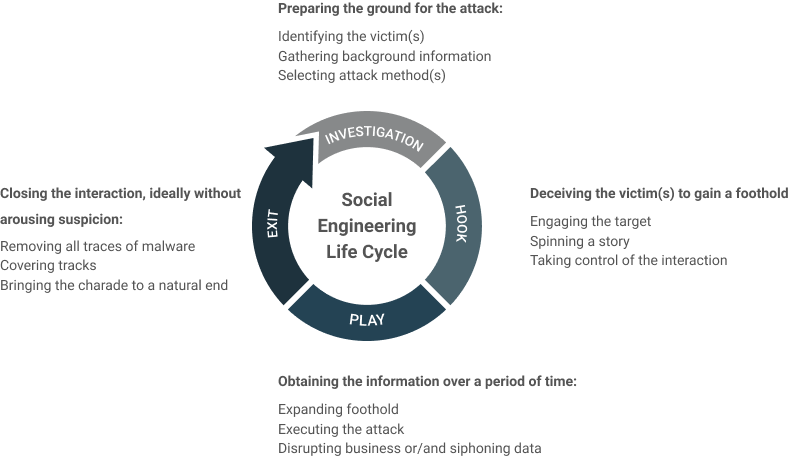
The goal of most hackers is simply to make money, although some have additional goals like damaging a company or organization's reputation or ability to carry out operations. In either case, the valuable asset they need is data.
Social engineering is a shortcut to help hackers acquire confidential data faster. They make personal contact with an individual, usually one who works at the organization they are trying to infiltrate. Then they'll use one of a number of schemes to gain unauthorized access into one more systems where a larger attack or virus can be initiated.
If you would like to find out more about other phishing types and techniques, please refer to our corresponding guide:
Further reading Methods and Types of Phishing Attacks


Social Engineering Methods
Overt Schemes
Email is by far the leader when it comes to instances of digital fraud. Many hackers choose to go the direct route and execute overt schemes on large groups of individuals. Even though a low percentage of these attacks are successful, the small number that takes the bait can result in a serious amount of damage.
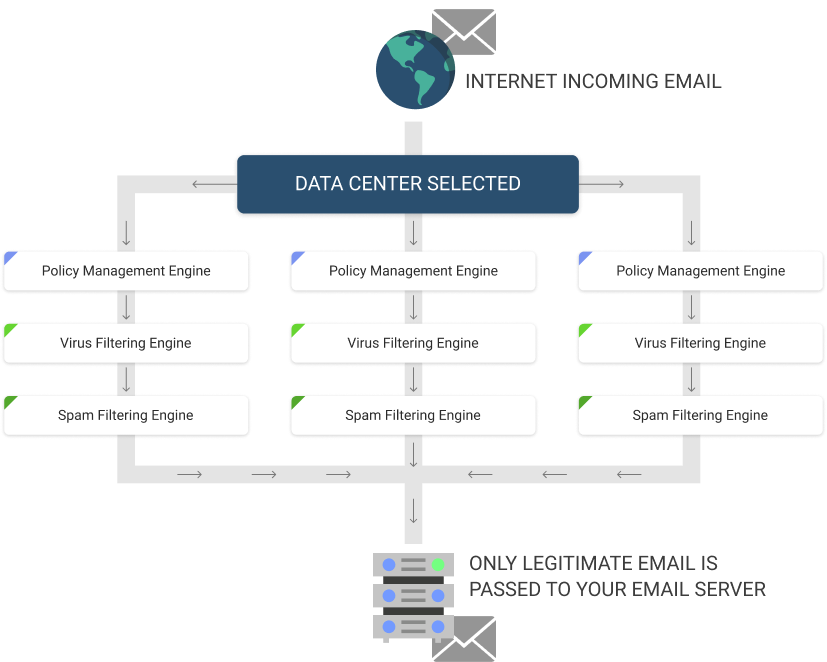
In a best-case scenario, your company or email provider has a strong filtering system that is capable of detecting fraud messages and moving them to a junk mailbox or blocking them entirely. But even the best filters are bound to miss some malicious content, which means you can never let down your guard.
Typically, an overt social engineering scheme will aim to tell a personal story via email that includes a request for action at the very end. For example, you may have received a spam message that claims to be from a friend or family member saying that they were mugged in a foreign city and need cash sent to them. This scheme is known as Londoning.
Other fraud emails will try to pose as legitimate business operations. They may try to sell you counterfeit goods or convince you to buy into an advance fee scam where they guarantee you will receive a certain amount of money. These types of attacks may seem ineffective, but even experienced internet users fall victim to them on a regular basis.
Don’t believe us? Dr. Phil deals with catfishing schemes at least once a week.
Covert Schemes
When overt schemes fail, cybercriminals look towards more covert methods for gaining access to data and money. While much social engineering is done through email, low- tech attacks carried out over the phone or face-to-face can yield big results.
In a covert social engineering attack, the hacker selects a specific individual as the target and then works to gain their trust. They may perform research online and look up the target on social media networks to understand where they work and live. They will usually target corporate users that have high-level administrative access to important back-end servers or databases.
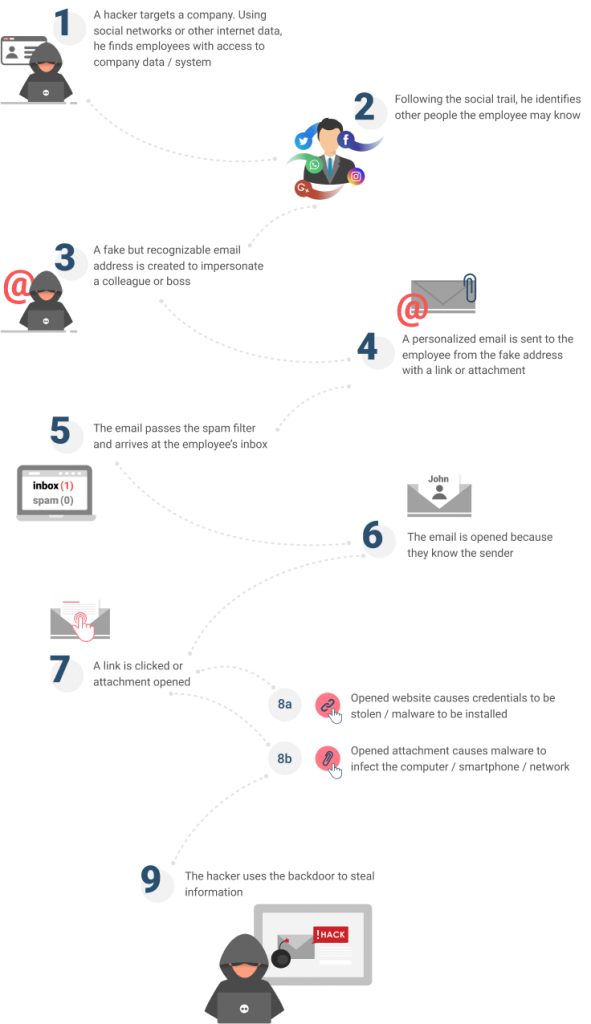
Once they have enough information, the hacker makes direct contact by phone posing as a customer or vendor who calls to resolve a “problem” with an account. One common ploy is for the hacker to encourage the target to download a certain piece of software so they can share screens and solve the problem together.
Learn how to implement a customer verification system:
Further reading Customer Verification for MSPs
Of course, the software download is malware and, just like that, a network is compromised.
Even sneakier is a current scheme making the rounds where the attacker sends a text, claiming to be from the target’s bank. The claim is made that a fraudulent transaction is suspected and the customer should just respond with a Y or yes in order that the problem could be investigated.
That mere one letter confirmation response is all that is needed to get the hacker into the account and create some actually fraudulent transactions.
When attacks are conducted via email it is called phishing. Usually, the message urges the reader to click on a link or respond with password credentials. Different method but the result is the same - a compromised network or account.
A successful social engineering attack often leads to a larger data breach or widespread hack. Ransomware is a common type of malware that hackers use to remotely encrypt data on a compromised computer. The owner of the machine will be prompted to pay a ransom in order to gain access to their data again.
Defending Against Social Engineering
IT security has evolved over the years, leading to a number of smart tools that can detect problems or breaches and alert the right people. Unfortunately, those types of solutions don’t protect against most forms of social engineering.
The onus for preventing these fall squarely on the individual or organization to provide preventative education and training.
Security should be emphasized as a priority across the entire organization. This can be a real challenge for large companies who have employees distributed across the globe with differing levels of access. For this reason, it's critical to protect your devices with a virtual private network (VPN) client.
A VPN serves as a good first line of defense in the war to protect our privacy online. It functions by creating a secure (encrypted) tunnel between your local machine and the open internet. It can serve as a safeguard against social engineering attacks because even if a hacker is able to infiltrate your local network, they will be unable to decode any of the content in the data they intercept.
For more information about phishing prevention, please read our guide:
Further reading Guide on How to Prevent Phishing
Final Thoughts
In a best-case scenario, social engineering is blocked at the initial point of attack, most successfully when the people in an organization are trained on how to identify attempts to target them.
Keep in mind that online security training is not a one-time thing. It should be repeated and reinforced on a yearly or quarterly schedule if possible and certainly made a major part of any new hire’s onboarding process.





