MSP360 Products
Security Considerations and Best Practices
It is sometimes thought that only big companies are affected by cyberattacks because their data might be worth a fortune. In fact, intruders may prefer smaller ones, since it is easier to compromise their security. When you’re working remotely with a company of any size, it is necessary to keep everything protected. Safety is our first priority, and we do our best for your data to be secure.
MSP360 Connect uses ports 80 and 443. Our servers are located in AWS, which is well known for its reliability and physical security. All the channels are encrypted and all the connections are secured by SSL. Additionally, we have developed our own security features. Below, we’ll describe how to set them up in the solution and also explain some practices that might be useful in our experience.

How to Set Up MSP360 Connect Security Features
When you create a custom build for a company, checking security options is a must. This helps you to protect your remote access, making it inaccessible to intruders. You can find these options in Downloads; click Download Build near Remote Desktop, in the Remote Computers Installation Package hit Remote Computers Installation, and proceed to the Security tab.
Here, you can see various PIN parameters, such as length or reset interval, so that it will be more difficult to find a match for those who don't know the PIN. But the main option here is the password. Click the Allow unattended access only with Custom Password checkbox and think up a password. This is strong protection because you have to enter the password every time you access the remote computer, which means it’s an additional layer of security. The permitted number of incorrect inputs is three; when an intruder exceeds this, the connection drops.
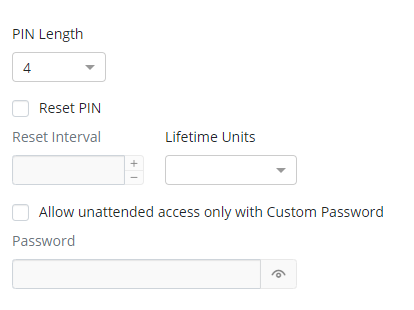
The PIN and password options allow you to protect data from your side. From the user's side, you can also set some restrictions. Go to the Limitations tab and sort out the options; you can limit access to configuration or GUI, so that no one will be able to change anything, intentionally or unintentionally.
MSP360 Connect Security Best Practices
There are several practices that it is worth implementing to keep your and your users’ data safe.
When you create a build, you can change the time it expires. We recommend using the default option – a week. If you choose a month or a year, it will be easier to compromise the safety of the build. Additionally, the passwords should be changed regularly, and after each change, you’ll need to generate a new build.
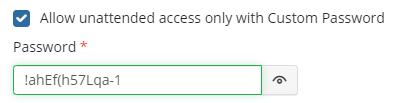
When you set up a password, make it strong. Use different capitalization, special symbols, letters, and digits.
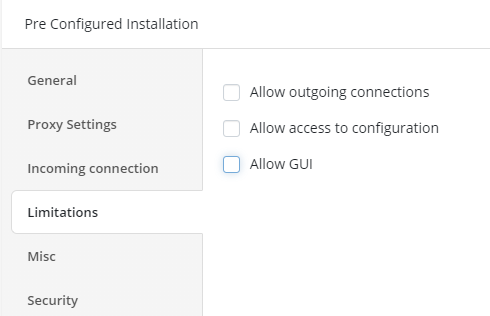
To protect the endpoints – your users’ computers – remove all the marks in the Limitations tab, so no one except you will be able to access the configuration and GUI on these PCs. The outgoing connections are also unnecessary for users, and these connections could be dangerous if an intruder were able to access them.
When you’re enabling remote access for users’ computers, remember that the data that is located there might be compromised via the Internet. To reduce the risks, use strong passwords and be sure that they are inaccessible to intruders.
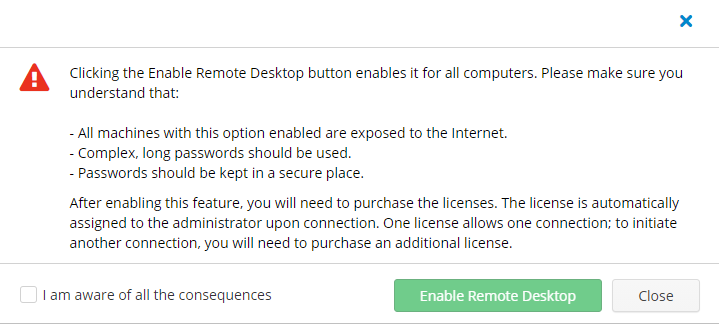
We value the safety of our solution above all. With Managed Connect, all your data is protected. If you have any remaining questions, please contact our pre-sales team.




