December 2019 has witnessed three major ransomware attacks on MSPs and service providers (and we're only halfway through the month!). The data of more than 100 dentistry practices was encrypted via an attack on an MSP, one of the biggest US data centers provider was hit and the data of several non profit organizations was encrypted with ransom demands of around $500,000.
How can MSPs protect themselves against attacks like these? One crucial step is to look for early warning signs. In some cases, one of the first signs of an incoming attack is that Windows security services are turned off.
With this in mind, one of our solution architects has developed a PowerShell script that will alert you if Windows Firewall is disabled.
You might also want to check the following article: Top 10 PowerShell Commands Every IT Admin Should Know.
About the Script
This PowerShell script works on a set schedule. It checks the status of the Windows Firewall and, if it’s disabled, sends an email message to the email address that you specify. The alert looks as follows:
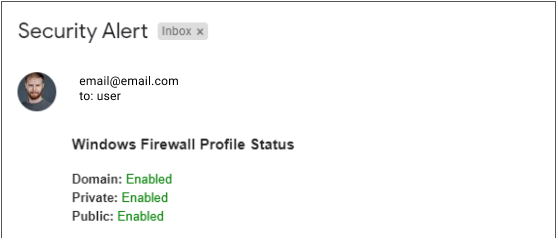
To run the script, you should have PowerShell 4.0 installed. It is installed by default on any Windows version including or higher than 8.1 To run the script on earlier OS versions, please update to Powershell 4.0 manually.
The script runs encoded, which adds security to the process. However, this also means that if you want to change the settings, you would have to restart the job.
Below you can find the script itself. Note that, to run it, you'll first need to enter several details.
The Script
#Requires -Version 4.0
#Script options
#Task scheduler job settings
$JobName = "Monitor Windows Security services" # Task scheduler monitoring job name
$JobUserName = "Domain\User" # Local admin username.
$JobUserPwd = 'User_Password' # Local admin password
$MonitoringJobSchedule = New-ScheduledTaskTrigger -At 07:00:00 -Daily # Get more about task trigger https://docs.microsoft.com/en-us/powershell/module/scheduledtasks/new-scheduledtasktrigger
# Email settings
$MessageFrom = "[email protected]" # Sender email address
$MessageTo = "[email protected]" # Recepient email address
$MessageSubject = "Security Alert" # Email subject
$MessageSMTPServer = "smtp.gmail.com" # SMTP server address
$MessagePort = 587 # SMTP port
$MessageUseSSL = $True # Use SSL?
$MessageUserName = "[email protected]" # SMTP server user
$MessageCredsPassword = 'Email_password' # SMTP server user password
# Monitoring settings
$IsFirewallMonitored = $True # Set $true to monitor Firewall settings or $false to skip
#Script
$MessageCredsPassword = $MessageCredsPassword | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString
$Script = "
`$MessagePwd = '$MessageCredsPassword' | ConvertTo-SecureString
`$MessageCreds = New-Object System.Management.Automation.PSCredential -ArgumentList $MessageUserName, `$MessagePwd
`$FirewallStatus = Get-NetFirewallProfile | Select -property Name, Enabled
if ((`$$IsFirewallMonitored -and (-not `$FirewallStatus[0].Enabled)) -or (`$$IsFirewallMonitored -and (-not `$FirewallStatus[1].Enabled)) -or (`$$IsFirewallMonitored -and (-not `$FirewallStatus[2].Enabled))){
if(`$$IsFirewallMonitored){
`$MessageBody = ""<H3>Windows Firewall Profile Status</H3>""
if(`$FirewallStatus[0].Enabled){`$MessageBody += ""<b>Domain: </b><font color=green>Enabled</font><br>""}else{`$MessageBody +=""<b>Domain: </b><font color=red>Disabled</font><br>""}
if(`$FirewallStatus[1].Enabled){`$MessageBody += ""<b>Private: </b><font color=green>Enabled</font><br>""}else{`$MessageBody +=""<b>Private: </b><font color=red>Disabled</font><br>""}
if(`$FirewallStatus[2].Enabled){`$MessageBody += ""<b>Public: </b><font color=green>Enabled</font><br>""}else{`$MessageBody +=""<b>Public: </b><font color=red>Disabled</font><br>""}
}
Send-MailMessage -From "+$MessageFrom+" -To "+$MessageTo+" -Subject ""`$env:computername $MessageSubject"" -Body `$MessageBody -SmtpServer "+$MessageSMTPServer+" -UseSsl:$"+$MessageUseSSL+" -Port "+$MessagePort+" -Credential `$MessageCreds -BodyAsHtml}"
$encoded = [Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($Script))
$action = New-ScheduledTaskAction -Execute 'Powershell.exe' -Argument "-NoProfile -WindowStyle Hidden -encodedCommand $encoded"
if(Get-ScheduledTask -TaskName $JobName -ErrorAction SilentlyContinue) {Unregister-ScheduledTask -TaskName $JobName -Confirm:$false}
Register-ScheduledTask -Action $action -Trigger $MonitoringJobSchedule -TaskName $JobName -User $JobUserName -password $JobUserPwd
Deployment, Alerts for Defender, Windows Updates and Antivirus
We also have prepared an enhanced version of the script that monitors the status of Windows Defender, Windows AutoUpdate and third-party antiviruses. In addition, we have provided a file that allows the deployment of the script through the RMM. Learn more and download the script.
Feel free to use or modify the script. And, if you have any questions regarding the script, let us know in the comments below.





