In this blog post, we will demonstrate how to grant users access to a specific folder in a bucket.
Table of Contents
First, you need to create an IAM user and assign a policy that will allow the user to access a specific bucket and folder:
Further reading How to Create IAM Users and Assign Policies
As an example, we will grant access for one specific user to the bucket named cloudberry.public and ”images” folder inside it.
Allow Required Amazon S3 Permissions
First of all, you need to specify permissions that are required for access to Amazon S3 - ListAllMyBuckets and GetBucketLocation. If these two permissions are not specified, the user will face the “Access Denied” error on each attempt to access any object within the bucket.
Policy required:
{
"Sid": "AllowUserToSeeBucketListInTheConsole",
"Action": ["s3:GetBucketLocation", "s3:ListAllMyBuckets"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::*"]
}
ListAllMyBuckets grants the user permission to list all the buckets in the AWS account. It is required for navigating buckets via the Amazon S3 console and CloudBerry Explorer.
GetBucketLocation grants the user permission to navigate within the AWS account via the Amazon S3 console and MSP360 S3 Explorer.


Allow Listing Objects in the Root Folder
Our user should have access to only one folder named “Images” but all the other folders within a bucket shall be visible for them. To have an ability to navigate objects within an S3 bucket we need to specify additional permissions. These permissions allow the user to view the contents of the root of the bucket:
{
"Sid": " AllowRootAndHomeListingOfCompanyBucket",
"Action": ["s3:GetBucketLocation", "s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::cloudberry.public"],
"Condition":{"StringEquals":{"s3:prefix":[""],"s3:delimiter":["/"]}}
}
ListBucket is required to specify a list of files and folders that will be visible to the user. Without the ListBucket permission specified user will face an access denied error each time trying to view the contents of the root of the bucket.
Note: The user won't be able to view the contents of any files or folders except his own.
The s3:prefix condition specifies files and folders that are visible to the user.
The s3:delimiter condition specifies a slash as a delimiter of the folder. It is not necessary to specify a delimiter but it is worth specifying as it will help to create folders and subfolders within a bucket in the future.
Allow Listing Objects in Images Folder
Now our users can view files and folders at the root of the bucket. We shall grant them access to all the objects in the folder and any subfolders that might be created in the future. For it we have to specify the following policy:
{
"Sid": "AllowListingOfUserFolder",
"Action": ["s3:GetBucketLocation", "s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::cloudberry.public"],
"Condition":{"StringLike":{"s3:prefix":["images/*"]}}
}
Allow All Amazon S3 Actions in Images Folder
Finally, we have to specify a list of user's actions that they shall be able to take with objects within a folder. We shall allow all the actions such as read, write, and delete permissions and limit them to just one folder - “images”.
{
"Sid": "AllowAllS3ActionsInUserFolder",
"Effect": "Allow",
"Action": ["s3:*"],
"Resource": ["arn:aws:s3:::cloudberry.public/images/*"]
}
“Action” element with “s3:*” specified allows the user to take all the Amazon S3 actions.
"Resource" element limits allowed actions to just one specified folder.
The whole policy for the user shall look like this:
{
"Statement": [
{
"Sid": "AllowUserToSeeBucketListInTheConsole",
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:ListAllMyBuckets"
],
"Resource": "arn:aws:s3:::*",
"Condition": {}
},
{
"Sid": "AllowRootAndHomeListingOfCompanyBucket",
"Effect": "Allow",
"Action": ["s3:ListBucket", "s3:GetBucketLocation"]
"Resource": "arn:aws:s3:::cloudberry.public",
"Condition": {
"StringEquals": {
"s3:prefix": "",
"s3:delimiter": "/"
}
}
},
{
"Sid": "AllowListingOfUserFolder",
"Effect": "Allow",
"Action": ["s3:ListBucket", "s3:GetBucketLocation"]
"Resource": "arn:aws:s3:::cloudberry.public",
"Condition": {
"StringLike": {
"s3:prefix": "Images/*"
}
}
},
{
"Sid": "AllowAllS3ActionsInUserFolder",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::cloudberry.public/Images/*",
"Condition": {}
}
]
}
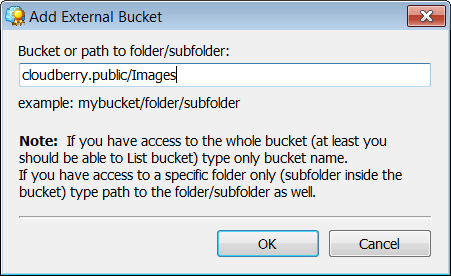
Create an External Bucket with CloudBerry Explorer
Now, the user should create an External Bucket. Note that the user can use CloudBerry Explorer freeware.
Specifying the bucket and the path:
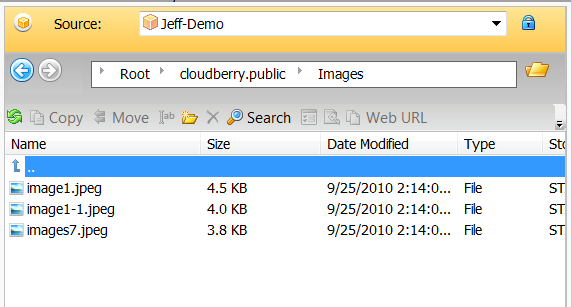
After that, they will be able to browse the content of the bucket and perform file operations allowed in the policy.
Note: this post applies to CloudBerry Explorer 2.7.5 and later.




