We are always trying to stay on top of the new functionality introduced by Amazon. In this guide, we will describe how to create and access Amazon S3 endpoint in your VPC.
Amazon Virtual Private Cloud (Amazon VPC) is the Amazon service that allows you to create and manage virtual private networks. By default, all AWS resources are accessed via the public Internet. You may need to restrict access to your cloud network due to security requirements of your project. Before now, you had to allow internet communications between your VPC and AWS resources that you need. The recently introduced feature called VPC Endpoints allows you to keep your VPC truly private and grant access only to the resources that you need directly from the network itself.
Everything about backing up to Amazon S3:

Creating Amazon S3 Endpoint in Virtual Private Cloud
To create an S3 endpoint, please follow the steps described below:
1. Open the Amazon VPC console. In the navigation pane, choose Endpoints.
2. The opened page will ask you to create your first S3 endpoint. Click the “Create Endpoint” button.
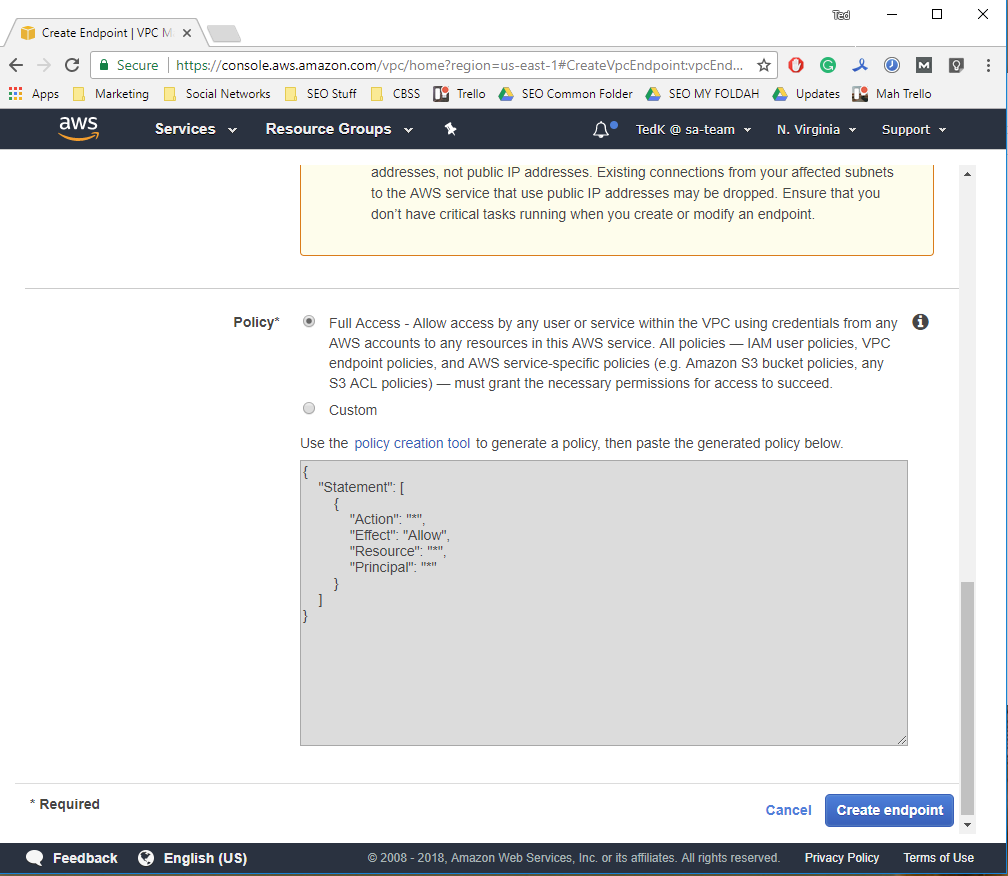
3. Choose your VPC and specify a policy that controls access to the AWS service. You can allow full access, or create a custom policy. Let’s go with full access.
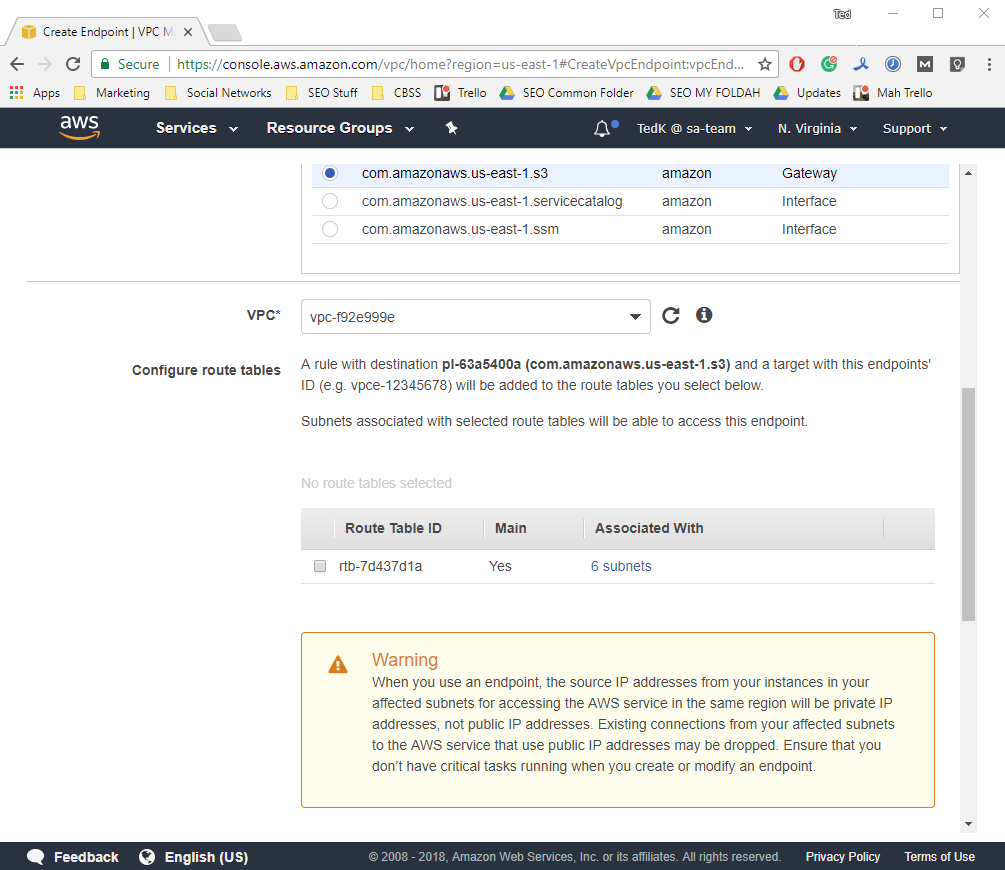
Also, you will need to select the route tables that will be used by the endpoint. All subnets associated with selected route tables will be able to access this S3 endpoint.
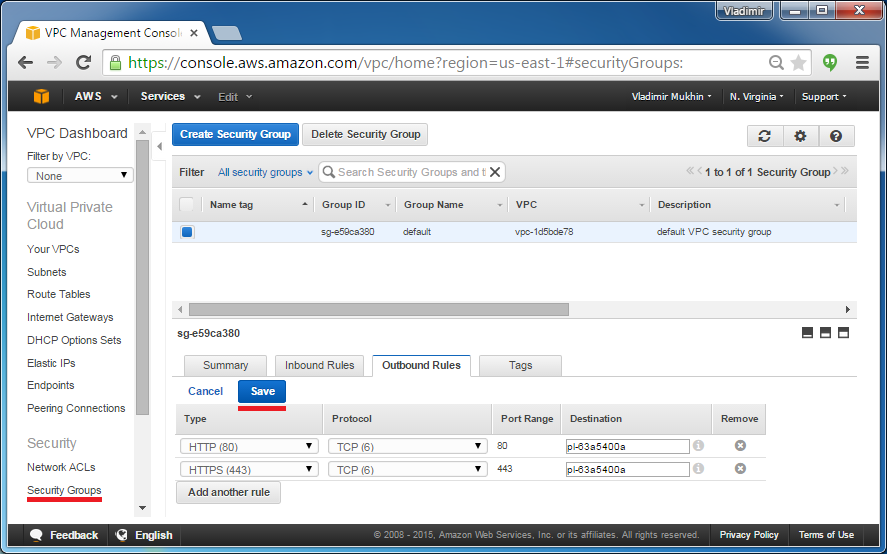
4. After you created your AWS S3 endpoint, you need to allow HTTP and HTTPS connections to this S3 VPC endpoint. Get back to the Amazon VPC console, click “Security Groups”, choose a security group associated with your Amazon S3 VPC, go to “Outbound Rules”, press “Edit”. You need to allow connections via ports 443 and 80 and specify your endpoint as a destination.
5. Ensure that your bucket is located in the exact same region as the EC2 instance. You can do that in the MSP360 Backup's settings. Select your S3 account on the main toolbar.
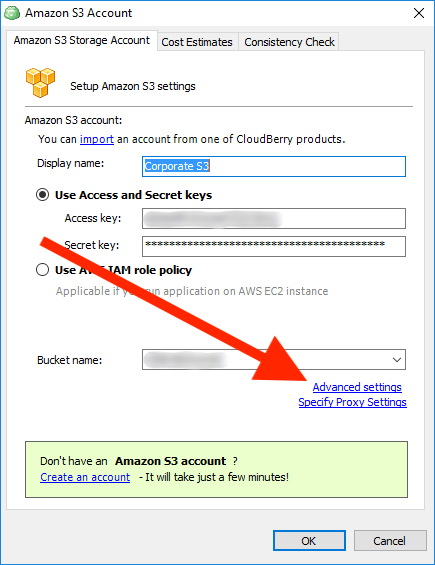
Click Advanced settings.
Expand the Primary region drop-down menu and select the region that matches the EC2 instance's region.
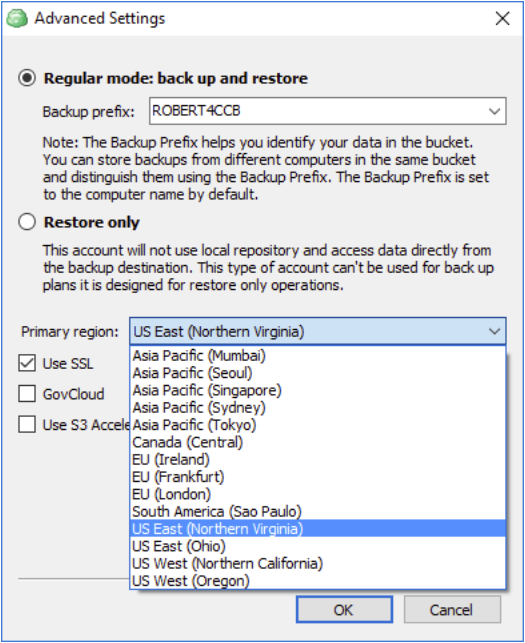
When you use an AWS S3 endpoint, the source IP addresses from your instances in your affected subnets for accessing the AWS service in the same region will be private IP addresses, not public IP addresses. Existing connections from your affected subnets to the AWS service that use public IP addresses may be dropped. Ensure that you don’t have critical tasks running when you create or modify an endpoint. To reiterate once again, ensure that your EC2 instance and S3 bucket are located within the same region, otherwise, VPC will not work.
When using single VPC, you will be able to access only the bucket of the region where this VPC is located. If you want to access buckets in multiple regions, you need to configure endpoints in every VPC for each region and connect this networks between each other by using VPC peering.
Summary
Our team provides maximum effort in order to suggest best cloud management tools and support all latest functionality released by major cloud storage providers. If you are interested in support for any feature provided by your storage provider, please let us know and we will be glad to consider your use case or suggestion.






