The recent coronavirus outbreak has led to one more loophole in your customers’ protection against phishing techniques. Hackers are impersonating health organizations to persuade users to download an infected file or leave their credentials on scam websites.
In this article, we will overview several email examples, provide you with details on where to find the latest valid information about COVID-19, and discuss how you should prepare your customers for the impending coronavirus phishing outbreak.
What Is Coronavirus Phishing?
Phishing is a malicious technique that malefactors use to gather sensitive user information, perform financial operations, or get access to corporate infrastructure. Here’s how it works.
Hackers send bogus emails in bulk or aimed at a person, group or organization. These emails are designed to fool recipients into believing that they were sent by a trusted party: a known vendor, a bank or a governmental facility, to name just a few examples. The body of such a scam email usually contains a downloadable malware file or a link to a website where a user is requested to “log in”.
Learn about other methods and types of phishing attacks:
Further reading Types of Phishing
With the outbreak of the new virus, malefactors are impersonating medical facilities and institutions in order to play on people’s fears. They are sending emails with “valuable statistics”, “latest news”, “urgent advice” or “free testing”. Your clients’ users may be trained to avoid typical phishing, but with the advent of this completely new and frightening danger that is spreading around the world, they might drop their guard.


How to Stay Safe from Coronavirus Phishing
Before we skip to the coronavirus phishing email examples, let’s review the top tips to stay safe from the attacks:
- If you are not subscribed to specific send-outs, medical or governmental facilities will not email your personal or corporate addresses, no matter how urgent it may be.
- If you have received an email from a known organization with the “latest news”, check its website for the up-to-date information.
- Generic greetings coupled with spelling and punctuation errors are usually a good sign of a scam email.
- Check the sender’s domain name. Typically, they try to make the name look like the original, but it still has some weird extension (such as gov.org, which is a clear sign that the sender is faking the typical US-governmental .gov domain).
- If you have opened the email, avoid clicking any buttons or links, or downloading any files there. If you do, the chances of getting hacked are just about 100 percent.
Further reading Phishing Response Guide
As a managed IT provider, you should not only pay attention to new phishing scams but, more importantly, draw your clients' attention to the tips and the examples that we will review next. The best way to do this is to create send-outs to your clients about the possible scams and provide training for their employees. A more thorough approach might include sending an email mimicking the real phishing email, to check if the users are ready for the approaching scam.
Examples of Coronavirus Phishing Emails
Coronavirus Phishing Email Example #1
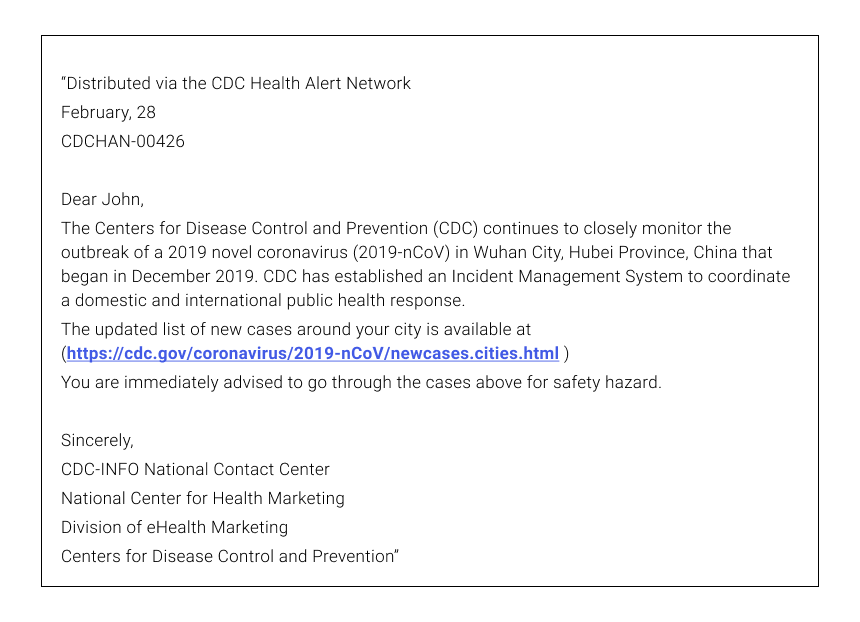
The first email claims to be sent from the CDC – Center for Disease Control and Prevention. This one is crafty since it uses some reference coding system to make it look realistic, as well as a personal greeting (“Dear X”), and it even provides a “valid” link to cdc.org. There are two ways to detect the scam here:
- The CDC wouldn’t send you personal emails. If you are not sure, visit their official website. It will have all the information about the “Incident Management System”.
- The link is most probably spoofed by a lookalike. It is easy to modify the link to make it look like the real one and to insert a link to a scam resource instead. To check for that, hover the mouse above the link and the real URL will be shown.
Coronavirus Phishing Email Example #2
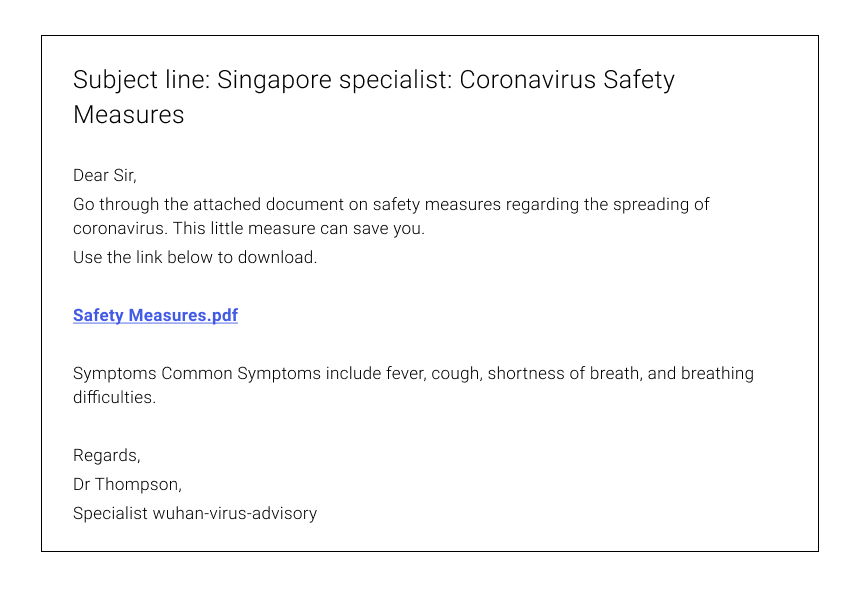
The next email is claimed to be sent by a ”Singapore Specialist”. Now, if you don’t know anyone from Singapore and haven’t subscribed to the specialist in question, that’s the first sign that you should avoid the email. The second is the downloadable file, which contains malware of some sort. The third is the lack of punctuation in the line: ”Symptoms Common Symptoms”.
Coronavirus Phishing Email Example #3
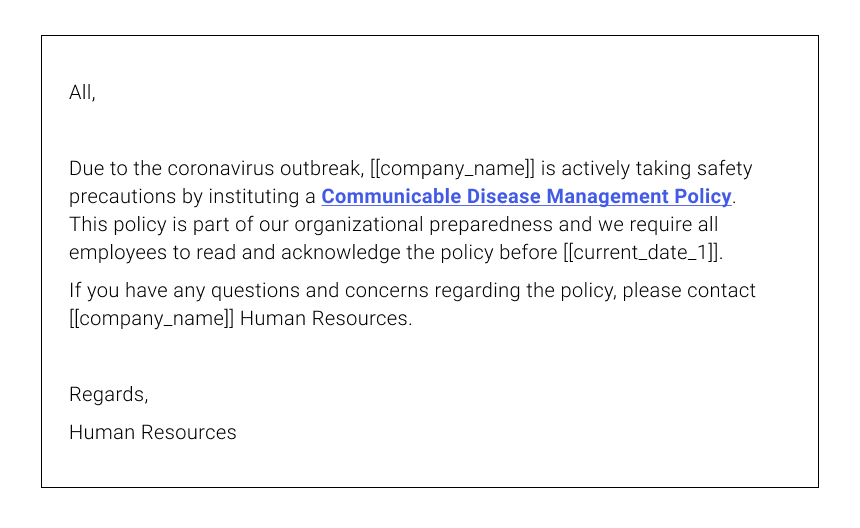
The third example is claimed to be sent from the company you work for and provides a fake log-in page where you should enter your credentials. The easiest way to expose it as a spoof would be to contact your management directly for any official news.
Coronavirus Phishing Email Example #4
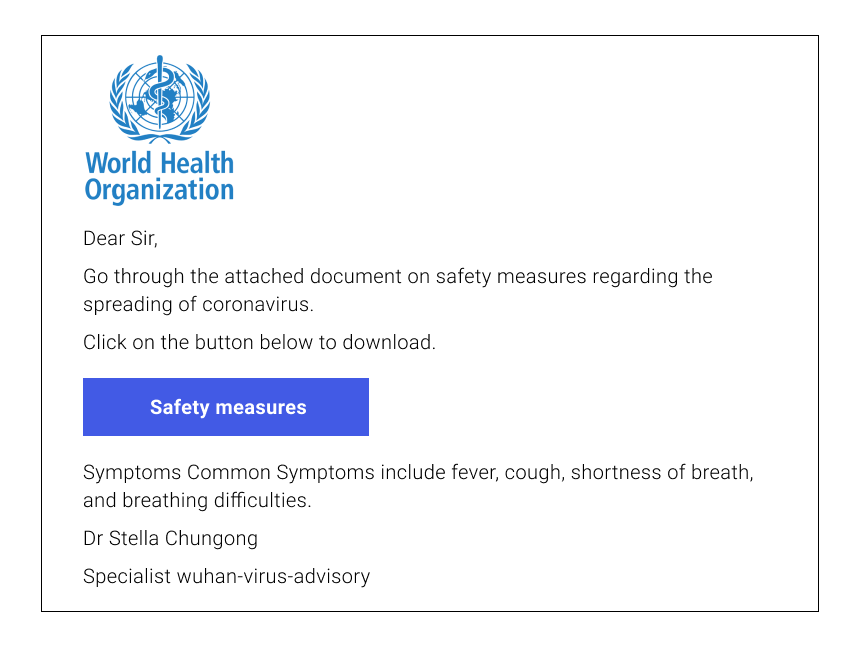
The last email claims to be sent from the World Health Organization. As we have previously said, organizations such as WHO wouldn’t send private or corporate emails. Check the sender’s email for possible spoof, and the website of the WHO to find the latest information on the topic. This particular email contains another glaring sign of a scam – several grammatical mistakes in the title text.
The World Health Organization would most probably spend a minute or two proofreading their official send-outs.
Where to Find Legitimate Information about the Coronavirus Outbreak
The other way you can help your clients is by providing them with actual information and resources about the COVID-19 virus. If they know where to get the legitimate information, there’s no reason for them to fall for any random email messages that they might receive. Here’s a list of useful sites with factual information about the COVID-19 virus.
- World Health Organization, or WHO, for short -- the world’s most readily recognized health organization.
- Center for Disease Control and Prevention (US). The CDC provides medical advice and up-to-date information about the coronavirus outbreak for US residents.
- National Health Service (UK). The NHS provides up-to-date medical advice, as well as specific advice to UK residents. Find out more information at their website.
The list of official resources will differ from one region to another. Look for reputable institutions in your geographical area and include them in the list.
Conclusion
Phishing has always been built around doubts and tricks. Nowadays, however, phishing attacks are based on the fear surrounding the new disease. The nature of fear means that it is stronger than simple doubt or negligence. This is why protecting and educating your customers about new types of scams is of the utmost importance.






