Attempts to infiltrate malware onto computers systems typically come from one of two sources: email and web sites. The most effective often use both. Phishes are one type of email used to attempt to get users to click on a link that will either get them to install malware or enter user credentials that can be used to infiltrate a real website.
These links or programs can install ransomware, sniffers, or Trojans that can steal information or hold it for ransom. These threats cost companies millions of dollars every year, and unfortunately, anti-virus programs may not catch all the threats.
For more information about phishing please refer to our guide on the topic:
Further reading Anti-Phishing Guide
The best way to prevent a malware infection is to keep a user from inadvertently downloading malware in the first place.
Phishes, in general, mock the look of genuine emails from legitimate sources, whether banks, corporate portals, online retailers, or other websites. Basic phishes mock the look of a legitimate email but generally won’t include an actual username or a person’s full name, address, or other information.
Spear phishes were the next generation of phishes, and they are specifically targeted to individuals, with enough information to appear legitimate at first glance, including the recipient’s full name, phone number, email address, etc.
Further reading How to Prevent Spear Phishing Attacks


Clone Phishing Definition
The next attempt to lull the recipient’s suspicions beyond spear phishes is the clone phishing. This uses an actual email that might have been intercepted as part of a legitimate stream of correspondence between a legitimate sender and the recipient that the bad actor is attempting to fool. Clone phishing can refer to a previous message that the recipient sent to the legitimate sender.
To find out about other phishing types and techniques, check out our corresponding guide
Further reading Methods and Types of Phishing Attacks
What Does Clone Phishing Look Like?
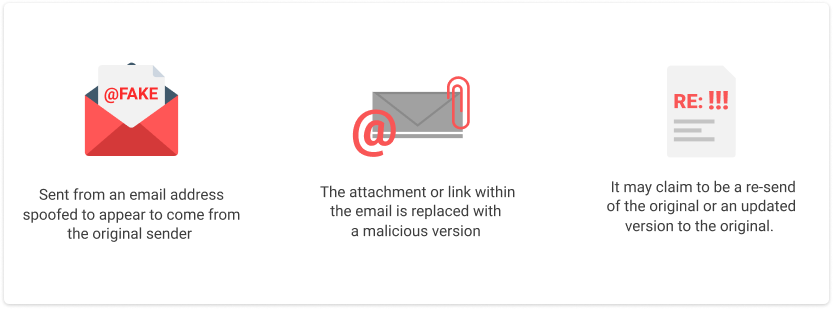
- Sent from an email address spoofed to appear to come from the original sender
- The attachment or link within the email is replaced with a malicious version
- It may claim to be a resend of the original or an updated version to the original.
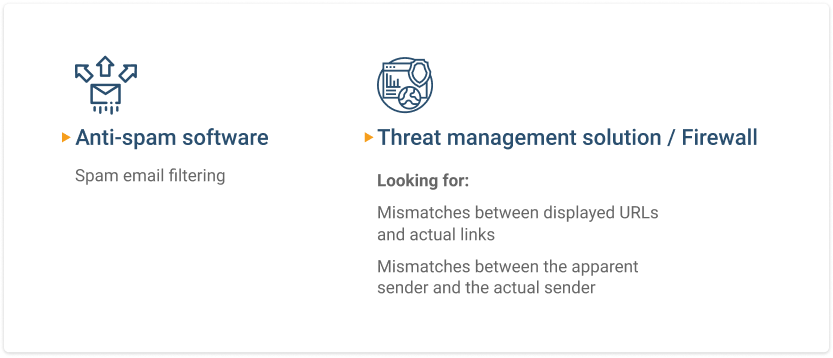
Preventative Measures
Two similar methods can be used to stop clone phishing. One filters all spam emails, and the other looks for mismatches between displayed URLs and actual links in the messages, as well as between the apparent sender and the actual sender.
The first is typical of an anti-spam appliance, while the second is typical of a unified threat management solution or firewall. While either solution can stop 99% or more of phishing emails, it’s always possible that clone phishing or another malicious email might slip through, so it’s a good idea to educate users on how to spot a malicious email as well.
For more phishing prevention best practices please refer to our corresponding guide:
Further reading Guide on How to Prevent Phishing
Signs That Can Help to Detect Malicious Email
 Hovering over a link in an email will show the actual URL, as opposed to the displayed link which may have nothing to do with the real email. The email program can also be set to display the actual sender rather than an alias – this will give a good indication that the email has been spoofed if the email address in the from box does not match the expected sender based on the original thread of the email.
Hovering over a link in an email will show the actual URL, as opposed to the displayed link which may have nothing to do with the real email. The email program can also be set to display the actual sender rather than an alias – this will give a good indication that the email has been spoofed if the email address in the from box does not match the expected sender based on the original thread of the email.
Further reading Coronavirus Phishing Awareness Guide
Educate Your End-Users
Regular training is the most effective method of keeping users apprised of the latest versions of malicious emails and other potential threats to corporate security. Educated users have a smaller chance of clicking on a malicious link or opening a malicious attachment. Since no security program finds every threat every time, this adds a needed dimension to corporate security.
Further reading Not Offering Anti-Phishing Training? Why Not?
Tell Users What They Should Do to Avoid Problems Once a Phishing Email Has Been Received
Some users will click on links despite regular training, and email security systems will occasionally fail to stop such things from getting through. In addition to helping users to identify clone phishing and other malicious emails, it’s also necessary to train them to enter URLs in the browser rather than clicking on links, even when the email seems legitimate.
Phishing Attack Simulation
One way to make the point on proper security procedures is to conduct simulated attacks. This creates a clone phish or other type of simulated malicious email and then reports to the email administrator and other leaders on which users succumbed to the attempts to collect credentials or who clicked on links in the email. These users can then be designated for remedial training, hopefully before they click on a malicious link.
Backup as the Last Line of Defense
One lesson learned from ransomware infections is that even if the ransom is paid, the files the ransomware encrypted may not be recoverable. In other cases, corporate policy or shortsightedness may prevent the ransom from being paid in the first place. A backup plan that has been well engineered and tested can protect you from the consequences of clone phishing attacks as well.
Conclusion
Unfortunately, like the Maginot line, network, and data system security can never provide perfect protection. The best chance a company has of surviving the increasing onslaught of malware is to combine all available technologies, test them thoroughly, educate users, and include backups.






