MSP360 Backup and MSP360 Explorer provide users with an ability to leverage the Amazon Identity and Access Management (IAM) service that allows you to create multiple users for one AWS account and specify access rights for each user or the set of users. Creating an Amazon IAM user with MSP360 ExplorerUse MSP360 Explorer PRO to create AWS IAM user. You can download a fully functional trial version, it is free for 15 days.
To start you’ll need an Amazon Web Services account configured in MSP360 Explorer. You can learn how to do that in our video tutorial.
1Open MSP360 Explorer PRO, navigate on Access Manager (IAM) on the toolbar and select New Policy Wizard.
2Select an AWS account you are going to work with.
3Create your IAM user and come up with a name for it.
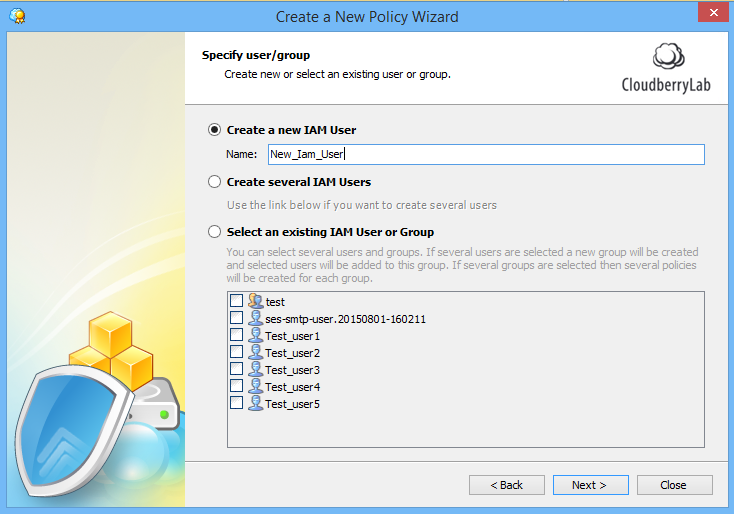
4Set up permissions for your IAM user. Just choose an appropriate option. For example, purposes we’ve chosen to grant read and write to selected buckets access to our AWS IAM user. Note: if you don’t want your user to see a list of all of your S3 buckets, uncheck the “Allow the user to access to AWS console” box. It will provide you with a better security level.
5Select the buckets to be used in this access policy.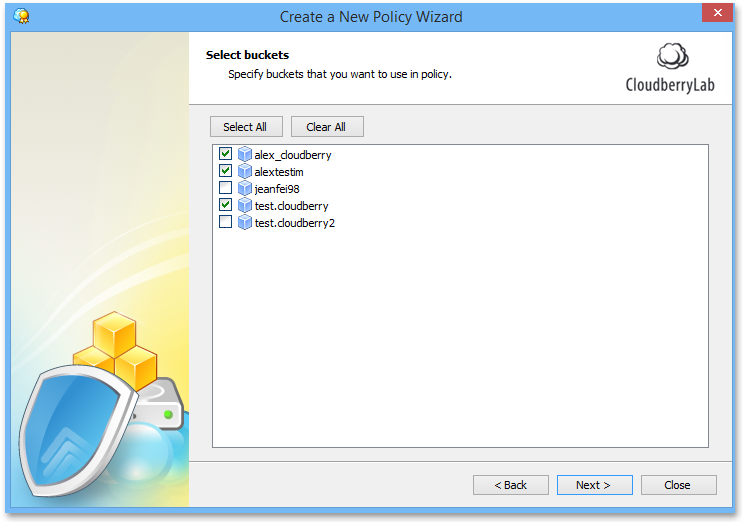
6Preview or modify the created access policy script.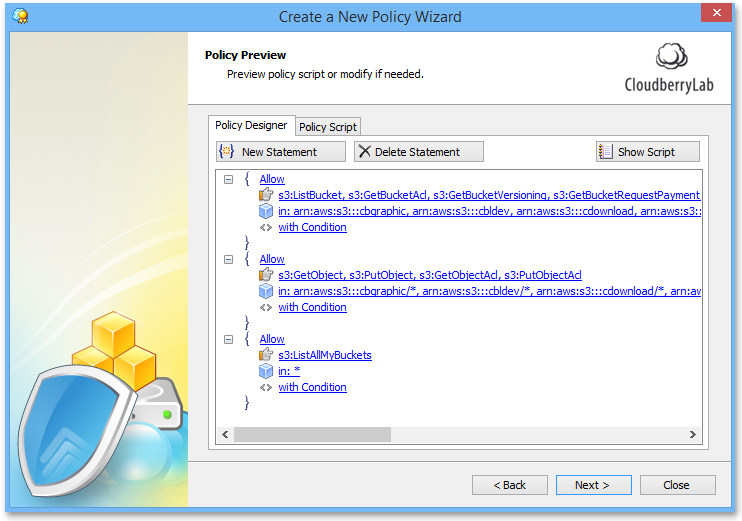 You can find the full policy script by switching to the Policy Script tab.
You can find the full policy script by switching to the Policy Script tab.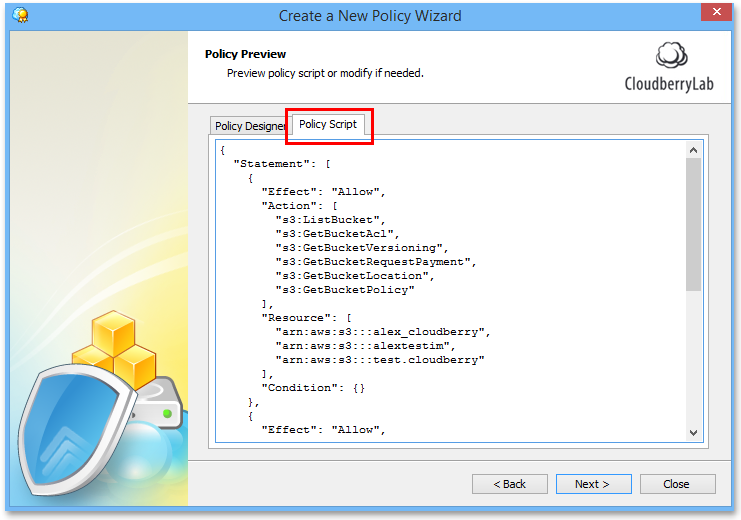 In our example, the script looks like this:
In our example, the script looks like this:
{
"Version":"2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketAcl",
"s3:GetBucketVersioning",
"s3:GetBucketRequestPayment",
"s3:GetBucketLocation",
"s3:GetBucketPolicy"
],
"Resource": [
"arn:aws:s3:::alex_cloudberry",
"arn:aws:s3:::alextestim",
"arn:aws:s3:::test.cloudberry"
],
"Condition": {}
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:DeleteObject",
"s3:DeleteObjectVersion",
"s3:GetObjectAcl",
"s3:GetObjectVersion",
"s3:GetObjectVersionAcl",
"s3:PutObject",
"s3:PutObjectAcl",
"s3:PutObjectVersionAcl"
],
"Resource": [
"arn:aws:s3:::alex_cloudberry/*",
"arn:aws:s3:::alextestim/*",
"arn:aws:s3:::test.cloudberry/*"
],
"Condition": {}
},
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*",
"Condition": {}
}
]
}
7Proceed with the Policy Wizard. After all the steps are completed you'll see the summary window. Now you’ve created your IAM user with limited permissions. To let this new user backup with MSP360 Backup, you need to create Access and Secret Keys for him. Follow the next instruction of this article to generate access keys!
Creating Access Keys
1Open MSP360 Explorer PRO, navigate on Access Manager (IAM) on the toolbar and select Access Manager.

2Choose your AWS account.
3Right click on your AWS IAM user and choose Manage Access Keys.
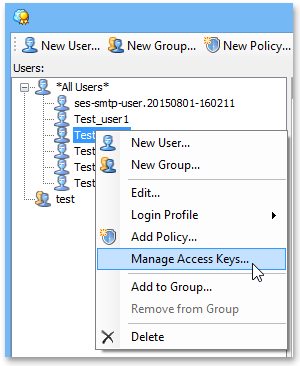
4In the opened window, click the Create button. Access Key and Secret Key for your IAM user will be generated automatically.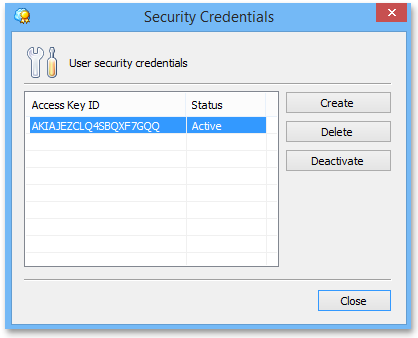
5Сopy your credentials to clipboard or save it to a file.
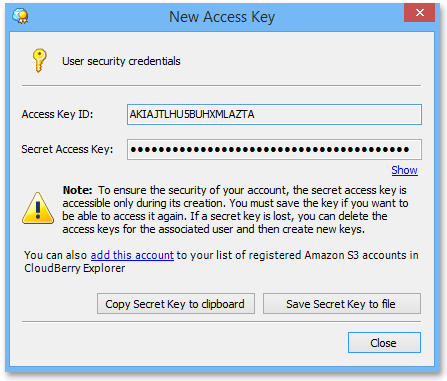
Applying IAM keys to MSP360 Backup
1Launch MSP360 Backup, click on the Menu Icon in the upper-left corner and click on the Add New Account button.
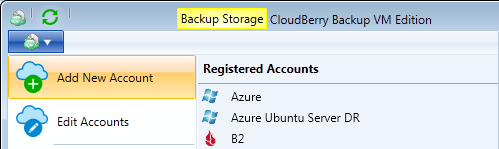
2In the "Select Cloud Storage" dialog, click on the Amazon S3 icon.

3Give your account a name in "Display Name" field (you can type any name you want), specify your "Access Key / Secret Key" pair and select a storage bucket from the "Bucket name" drop-down menu.
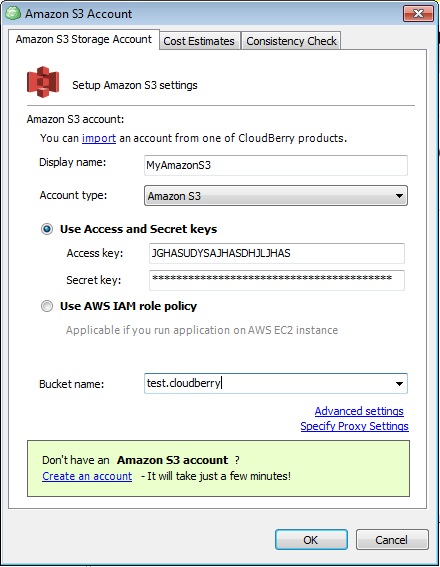
Now your MSP360 Backup user will have access with configured permissions only to a specified location in your S3 account.




