Encryption is everywhere: On your storage, on your network, over the Internet, and in the cloud. Encryption is about protecting your data from those who might otherwise use it to cause harm. It protects you from those who bypass security to access data within your organization, illegal access from outside, and provides protection for compliance. Your live data is the lifeblood of your organization and your backups protect your live data by letting you restore misplaced, damaged, stolen, or incorrectly edited data with versions that keep the business running.
Reason to Use Backup Encryption
Instead of asking why you should encrypt your backups, you might be better off trying to justify the reverse. Ask yourself, “Why shouldn’t I encrypt my backups?” It’s harder to come up with a justifiable reason. And if you leave it at that, then you're encrypting. And that’s the right decision.
Learn about backup storage and solutions in our guide:

How Do You Want to Encrypt Backups?
Two basic backup encryption technologies help protect your backups: Source-side data encryption and server-side encryption. Source-side data encryption uses customer-controlled keys to encrypt your data before it leaves your server or network. In MSP360 Backup, that means protecting your data with 256-bit AES encryption. The Advanced Encryption Standard is used worldwide and back in 2003 the U.S. Government announced it was secure enough to protect classified data. It’s a symmetric algorithm, meaning the same key is used to encrypt and decrypt your data.
Think of the encryption key as the combination that opens the safe.
What happens if you lose your backup encryption key? In that case, you're out of luck. Without it, you're not going to be able to decrypt your backups. Not in your lifetime anyway. Which brings up the one administrative item you do need to do. And that tracks your encryption key usage. You'll need to keep these keys in a secure location (which may be a password safe or an encrypted document with limited access).
What is a Backup Encryption Key?
What are these encryption keys and what do they look like? They are like passwords with combinations of letters, numbers, and symbols. They could be as simple (and insecure) as using the letter “a”, something complex and impossible to remember like “Da^\^K1'8Uay7pFIq:1S” or a memorable passphrase like “when.1.wasYoung-I-likedToGoOnROLLERcoasters”. There's no shortage of articles on the internet about password / key length and complexity. The important thing to remember is, the longer the key, the harder it is to crack the backup encryption with a brute force attack.
With your backups encrypted, only those with both access to the backup files and the backup encryption keys can decrypt your data.
How Does Server-Side Encryption Work?
Server-side encryption (SSE) is about protecting your data at rest at the storage level. It’s a feature that’s offered by many of the cloud storage providers. It has a few different names: Amazon S3 calls it Server-Side Encryption. Microsoft Azure calls it Storage Service Encryption. Google Cloud Platform calls it Encryption at Rest. Google enables the feature by default but with Amazon and Microsoft, it can be enabled with a single click. All implementations use AES with 256-bit keys. And it’s free.
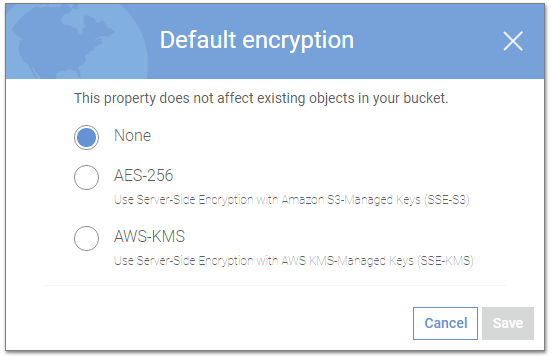
Server-side encryption options in Amazon
So, what's it doing and why should you care? Server-Side Encryption automatically encrypts data when it arrives, stores the data on disk, and automatically decrypts the data when it leaves - using backup encryption keys managed by your cloud service account. There are options on many cloud providers where you can manage keys, but for now, we'll discuss the simplest implementation.
The data on the disk is encrypted. Think of this as transparent backup encryption with no passwords to remember. It’s an added layer of encryption that involves a click (or in the case of Google, nothing). The best example of its value is this: You put an important business document in cloud storage, but you do not perform any source-side encryption. Maybe you need to access the file as-is from external sources or maybe you simply forgot to enable source-side data encryption. In either case, server-side encryption automatically encrypts the file and stores it on disk – transparently to you. If someone should break into the cloud storage facility and steal a hard drive, the data is safe – even without you applying your own encryption. Anyone with raw data access will not have access to the service controlled backup encryption keys and will not be able to do anything with the raw data on disk. Your file is safe.
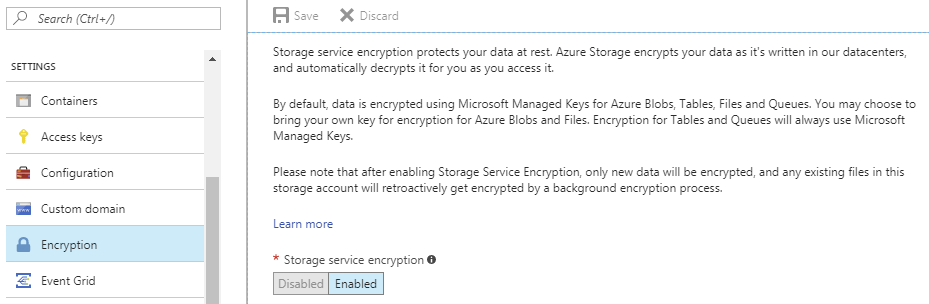
Server-side encryption options in Microsoft Azure
But if you're encrypting your backup data first, is there a need to also use server-side encryption? The short answer is, yes. It’s an added layer of protection, it’s free, and it’s transparent. So why not? It’s better to have two layers of backup encryption than one – especially if one comes with no administrative overhead or cost.







