In release 4.9, MSP360 Backup for Microsoft 365 / Google Workspace introduces shared mailbox licensing that aligns directly with Microsoft’s model. The update removes unnecessary backup licensing for shared mailboxes that Microsoft itself allows to operate without a license, improving MSP360 pricing transparency.
Table of Contents
What changed in the release 4.9
Previously, MSP360 Backup for M365/Google required a backup license for all shared mailboxes (like support@, sales@, billing@, hr@), regardless of Microsoft 365 licensing status. In Microsoft 365, shared mailboxes can be used without a license under specific conditions:
- It has no Microsoft 365 license assigned, and
- Its size remains below 50 GB.
In release 4.9 of MSP360 backup for M365/Google, shared mailbox licensing follows the same Microsoft rules.
If either condition is no longer met, you must have a backup license.
How MSP360 Backup for M365/Google applies the rules
The system detects shared mailbox status and Microsoft 365 license assignment during user synchronization.
The system validates mailbox size against the Microsoft 365 threshold:
- Microsoft 365 mailbox data, and
- MSP360 backup-side data, to prevent retention-based overuse.
This enforces the 50 GB threshold consistently and prevents large mailbox data from remaining in backup after Microsoft 365 removes it.
Mailboxes converted from standard users to shared mailboxes are reclassified after synchronization. You may need to release previously assigned backup licenses manually, depending on the tenant’s existing licensing state.
Note: You must have at least one currently assigned user backup license activated within your tenant at all times in order for backups to run successfully. Failure to have any user licenses assigned to your tenant will cause the tenant to become inactive, which could eventually lead to your account being suspended or removed for inactivity.
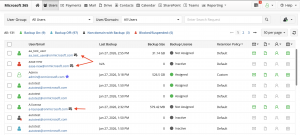
Shared mailbox visibility in the console
Shared mailboxes will now have their own icon in the user list in the MSP360 backup console for easy identification.
What happens when conditions change
- MSP360 Backup for M365/Google requires a Backup License for shared mailboxes over 50 GB or licensed with a Microsoft 365 license.
- If no backup license is available, the mailbox backup may stop with a No License Available status.
- Microsoft surfaces its limitations (for example, mailbox size constraints) as error messages.
Licensing changes take effect after the next user sync.
Key benefits
With Release 4.9, MSP360 Backup for Microsoft 365/Google Workspace users get:
- Clear and predictable licensing aligned with Microsoft 365
- Lower backup costs for environments with many shared mailboxes
- Reduced licensing friction during audits, renewals, and onboarding
- Better admin visibility inside the MSP360 backup console