Some EU customers don’t just ask where data is stored. They ask who can operate the cloud environment, how access is governed, and what happens under regulatory pressure.
MSP360 Managed Backup software 5.8: New Restore Plan Wizards and more
With MSP360 Managed Backup 5.8, we’re introducing the new web-based restore plan wizards that are compatible with the new backup format. The new version also comes with consistent date and time format across the web console, improved scheduling options for the new backup format, and a new name for our remote desktop solution.
Continue reading
MSP Guide for Cyber Incident Reporting and Critical Infrastructure Act
For MSPs, detecting and documenting cybersecurity incidents has always been important. But now, it’s a formal legal requirement in some cases, thanks to the recently enacted Cyber Incident Reporting for Critical Infrastructure Act of 2022. Continue reading
MSP360 Connect 3.0: Our New Remote Desktop, a New Edition, and More
We’re excited to announce that Remote Desktop has a new name, MSP360 Connect, and it’s more powerful than ever. MSP360 Connect is our simple and secure remote administration and support product. Continue reading
How to Start Your MSP360 Connect Pro Trial
Start a free, 15-day Connect Pro trial right in the MSP360 Connect app installed on your computer.
If you are not a Connect user yet, please download and install the app first.
Open Connect on your computer and click on the menu in the upper-left corner.

Click on Manage License.

In the window that appears, choose Start 15 days trial and then click Next.
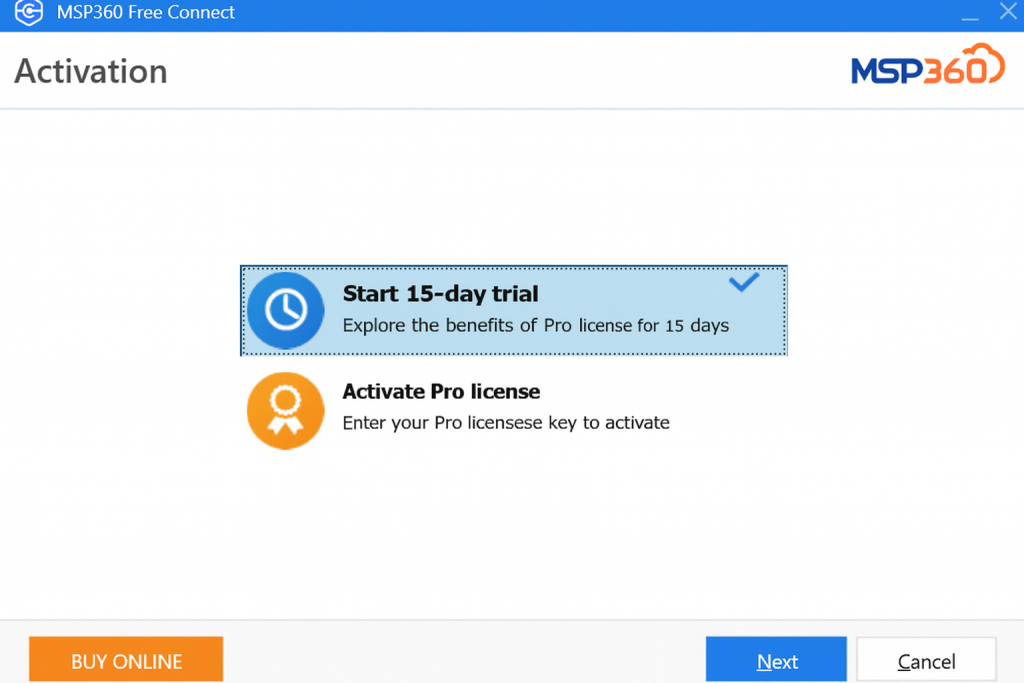
Enter your email address and click Start Trial.

That’s it. Please contact us if you have any questions.
Getting Started with MSP360 Connect (Free and Pro)
In this article, you will learn how to connect to a remote computer using MSP360 Connect and start using its features. Continue reading
Getting Started as a One-Person MSP: Here’s What to Consider
When it comes to starting a managed services provider (MSP) business, you can build it as a team or do it alone. While there are many benefits to collaborating with others, sometimes the “lone-wolf” approach can have immense benefits. But before going out on your own and becoming a one-person MSP, you should properly weigh the pros and cons of the decision. Continue reading
Why MSPs Should Reassess Their Cybersecurity Strategies in 2024
Cyberattacks have dominated headlines over the past year (and more), showing the very real risk that faces organizations of every size and shape today. These attacks have caused massive data loss, crippled critical infrastructure systems, stolen money and hindered hospitals’ ability to provide care, among many other impacts. Continue reading
Points to Consider when Buying an MSP Business
There are two fundamental ways to go about creating an MSP business. First, you could meticulously construct the business from the ground up, building out a list of clients and services from nothing. Continue reading
Why Training Your MSP’s Employees is More Important Today than Ever
When it comes to building a successful managed services provider (MSP) business, it’s often more about the people than the technology. Continue reading
Are You Doing Enough for Cybersecurity?
You only have to turn on the TV or open the morning newspaper to understand the impact that cyberattacks are having on businesses and individuals around the world. In 2021 alone, there were a reported 1,862 successful data breaches, up nearly double from the previous year, and the corporate world was experiencing approximately 925 attacks per week on average. Continue reading
Are You Simulating Disaster Scenarios Regularly?
Going through a sudden disaster or an emergency is one of the most terrifying things a business can experience, especially if the business is unprepared for it. For this reason, it’s essential for a small or medium business (SMB) to take the necessary precautions not only to implement disaster recovery plans and solutions but also to test them on a regular basis to confirm their effectiveness. Continue reading